LDAP/AD Server
-
For interest, Hetzner will add the ISO to your account "Project(s)" as an available image to mount from, if you just email their support with the ISO url, ie:
Contabo will too - you just need to specify it in the notes on the checkout and add €25 for a Custom build setup in the options.
Having only just discovered this UCS from @luckow 's nice recommendation. I now find myself quite interested in the KVM Apps too:
- https://www.univention.com/products/univention-app-center/app-catalog/kvm/
- https://www.univention.com/products/univention-app-center/app-catalog/uvmm/
We're just setting all this up now, so will report back on any discoveries.
@marcusquinn Don't get to excited about the uvmm app. Its discontinued for their next release. But most Univention users are using Proxmox for it anyways.
https://www.univention.com/blog-en/2020/12/ucs-5-0-discontinued-features/
-
@marcusquinn Don't get to excited about the uvmm app. Its discontinued for their next release. But most Univention users are using Proxmox for it anyways.
https://www.univention.com/blog-en/2020/12/ucs-5-0-discontinued-features/
@fbartels said in LDAP/AD Server:
Proxmox
Oh, thanks for the headsup. Is that this? https://www.univention.com/products/univention-app-center/app-catalog/sep-sesam/
I only started looking at USC for LDAP services for 3rd party apps to integrate with like Unify. Now I'm down a rabbit hole of what else it can solve

-
@fbartels said in LDAP/AD Server:
Proxmox
Oh, thanks for the headsup. Is that this? https://www.univention.com/products/univention-app-center/app-catalog/sep-sesam/
I only started looking at USC for LDAP services for 3rd party apps to integrate with like Unify. Now I'm down a rabbit hole of what else it can solve

@marcusquinn No, this is Proxmox. https://proxmox.com/en/
Sesam is a backup application, not a machine management solution.
-
@marcusquinn No, this is Proxmox. https://proxmox.com/en/
Sesam is a backup application, not a machine management solution.
@fbartels Nice! You like it?
Would it be naive thinking to try building a HA cluster based on multiple VPS instances across multiple providers?
-
@fbartels Nice! You like it?
Would it be naive thinking to try building a HA cluster based on multiple VPS instances across multiple providers?
-
@marcusquinn Installing Proxmox on an already virtual server to create a ha cluster: yes, i think that would be naive.
Installing Proxmox on real hardware, spread over multiple data centers: that is what it was made for.
@fbartels Cool - for performance, certainly agreed.
I was just thinking for testing purposes, I like to have a sandbox / staging version of everything we do, so not much point firing up 4 x bare metal racks with setup charges and minimum contracts just for that.
I guess the only way, as with everything is just try it and see what happens.
Back to the original thing with the need for LDAP. Do you or @luckow have any pointers on how we get UCS to see the outside world?
Looks like we need to expose port 636 but not found where yet. Anything else to be aware of?
-
@fbartels Cool - for performance, certainly agreed.
I was just thinking for testing purposes, I like to have a sandbox / staging version of everything we do, so not much point firing up 4 x bare metal racks with setup charges and minimum contracts just for that.
I guess the only way, as with everything is just try it and see what happens.
Back to the original thing with the need for LDAP. Do you or @luckow have any pointers on how we get UCS to see the outside world?
Looks like we need to expose port 636 but not found where yet. Anything else to be aware of?
@marcusquinn personally i would try to connect to port 7636 instead as this is where their openldap is always listening (if you install their samba 4 ad mode, then samba would be listening at 636 instead).
Ucs has a firewall locally where these ports may need to be allowed for outside access, although on my test system they are generally open Soni don't think there is a default rule in place to close it down.
Then i would create a machine account for the cloudron host and use this account for the cloudron sided configuration.
-
@marcusquinn personally i would try to connect to port 7636 instead as this is where their openldap is always listening (if you install their samba 4 ad mode, then samba would be listening at 636 instead).
Ucs has a firewall locally where these ports may need to be allowed for outside access, although on my test system they are generally open Soni don't think there is a default rule in place to close it down.
Then i would create a machine account for the cloudron host and use this account for the cloudron sided configuration.
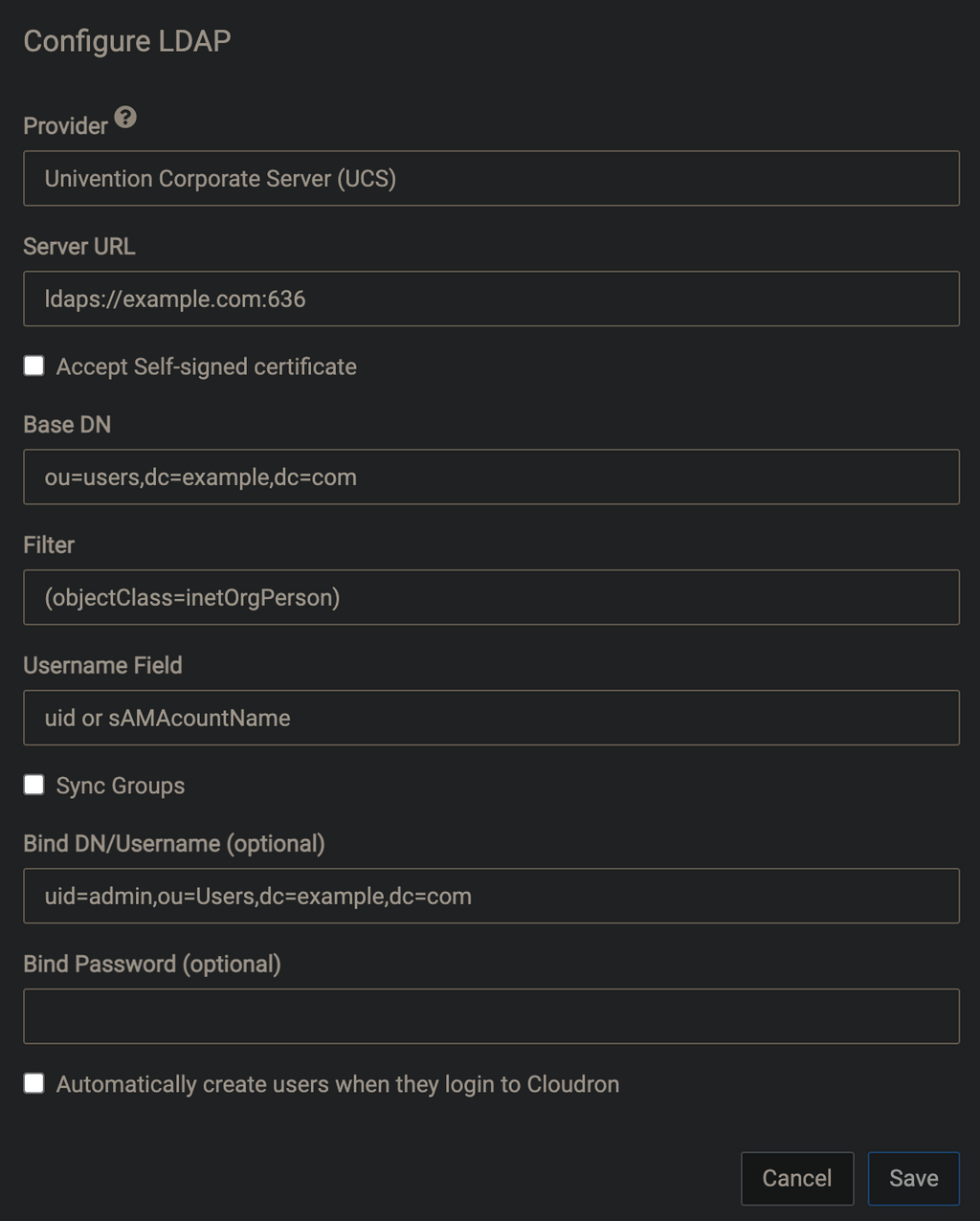
@fbartels Thanks, I'm running completely blind on this as I've not really found any documentation that gives any certainty on what's necessary or not, as one imagines every field has a reason and necessary action to create and highlight each value at the UCS end.
https://docs.cloudron.io/user-management/#external-ldap
-
@fbartels Thanks, I'm running completely blind on this as I've not really found any documentation that gives any certainty on what's necessary or not, as one imagines every field has a reason and necessary action to create and highlight each value at the UCS end.
https://docs.cloudron.io/user-management/#external-ldap

@marcusquinn I can imagine that the fields do not make much sense, if one has not really worked with ldap before.
Something like the following should work:
Server URL: ldaps://$your-univention-fqdn:7636 [x] Accept Self-signed certificate (since the univention ldap has a certificate from the ca on the univention system, better would of course be to import the univention ca on the cloudron host) Base DN: cn=users,dc=your-univention,dc=fqdn Filter: (objectClass=inetOrgPerson) Username Field: uidFor the bind user I would again recommend to create a machine account on UCS. This is done from their management ui -> devices -> computers.
Click "add" select "Computer: Linux" as type and give the entry a name (for example "Cloudron"). After the item has been created open it and go to "Advanced settings" and unfold the "Account" entry. Here you can specify a password for your user.Bind DN/Username (optional): cn=Cloudron,cn=computers,dc=your-univention,dc=fqdn Bind Password (optional): your choosen passwordNow you can click on save on Cloudron and hit that sync button. If all worked out you should now see your ucs users (like their default
administratoruser) in the user list of your cloudron. These external entries have then a small addressbook picture behind their name to differentiate them from the native Cloudron users.@nebulon feel free to use the above in your instructions at https://docs.cloudron.io/user-management/#external-ldap
edit: since were on the topic. I am using the following settings to sync groups as well:
Group Base DN: cn=groups,dc=your-univention,dc=fqdn Group Filter: (objectClass=univentionGroup) Groupname Field: cnThis then also gets some internal groups like "computers" and "printer-admins", but that does not bother me much.
-
@marcusquinn I can imagine that the fields do not make much sense, if one has not really worked with ldap before.
Something like the following should work:
Server URL: ldaps://$your-univention-fqdn:7636 [x] Accept Self-signed certificate (since the univention ldap has a certificate from the ca on the univention system, better would of course be to import the univention ca on the cloudron host) Base DN: cn=users,dc=your-univention,dc=fqdn Filter: (objectClass=inetOrgPerson) Username Field: uidFor the bind user I would again recommend to create a machine account on UCS. This is done from their management ui -> devices -> computers.
Click "add" select "Computer: Linux" as type and give the entry a name (for example "Cloudron"). After the item has been created open it and go to "Advanced settings" and unfold the "Account" entry. Here you can specify a password for your user.Bind DN/Username (optional): cn=Cloudron,cn=computers,dc=your-univention,dc=fqdn Bind Password (optional): your choosen passwordNow you can click on save on Cloudron and hit that sync button. If all worked out you should now see your ucs users (like their default
administratoruser) in the user list of your cloudron. These external entries have then a small addressbook picture behind their name to differentiate them from the native Cloudron users.@nebulon feel free to use the above in your instructions at https://docs.cloudron.io/user-management/#external-ldap
edit: since were on the topic. I am using the following settings to sync groups as well:
Group Base DN: cn=groups,dc=your-univention,dc=fqdn Group Filter: (objectClass=univentionGroup) Groupname Field: cnThis then also gets some internal groups like "computers" and "printer-admins", but that does not bother me much.
@fbartels Thanks - so far UCS is a long way from intuitive. I feel like I got invited around for dinner and pointed at the kitchen while everyone else already ate.
It seems strange to have to install an App for Lets Encrypt, as in that should just be a standard feature enabled for all to use or ignore.
I have a feeling we're going to have to start again with reimagine this VPS because guesswork setups and issues are costing way more time that expected.
The world really doesn't like solving the obvious needs in obvious ways.
Really appreciate the instructions as I'm tearing my hair out with now over a day on something that I really don't think should be this complicated.
It's like we have to deal with developers that think: "Well, we could make that possible, but since no-one has explicitly campaigned for it, lets just say its possible but not actually solve it, so everyone has to either learn everything we already know, or spend more time convincing us to make something obvious, then we might think about."
My only sanctuary in persevering with all this, is that with Microsoft, Google & AWS they'd also try and sell you some certified course nonsense as well before allowing you to play their specifically different ways.
-
@fbartels Thanks - so far UCS is a long way from intuitive. I feel like I got invited around for dinner and pointed at the kitchen while everyone else already ate.
It seems strange to have to install an App for Lets Encrypt, as in that should just be a standard feature enabled for all to use or ignore.
I have a feeling we're going to have to start again with reimagine this VPS because guesswork setups and issues are costing way more time that expected.
The world really doesn't like solving the obvious needs in obvious ways.
Really appreciate the instructions as I'm tearing my hair out with now over a day on something that I really don't think should be this complicated.
It's like we have to deal with developers that think: "Well, we could make that possible, but since no-one has explicitly campaigned for it, lets just say its possible but not actually solve it, so everyone has to either learn everything we already know, or spend more time convincing us to make something obvious, then we might think about."
My only sanctuary in persevering with all this, is that with Microsoft, Google & AWS they'd also try and sell you some certified course nonsense as well before allowing you to play their specifically different ways.
@girish Classic example of platform gatekeeping decisions costing every user the same inordinate amount of time.
Option 1: Cloudron does not block external LDAP access. We can then use that with non Cloudron apps and get on with our lives.
Option 2: Find someone that knows another platform that might do what could already be done with Option 1, if we are "allowed", then learn all the curiosities of that other platform and maintain it, just for one tiny single feature, that we could have with Option 1, if your discretion allows.
So far option 2 has cost myself and another person the last 2 days work lost from doing anything else that we would have otherwise been progressing.
OK, so we will learn another platform, and it might have some other useful features - but it is a forced situation based on platform owner decisions more than user needs.
Sorry to share the frustrations upstream, but I just see extraordinary value from the simplicity of this being solved, versus vast amounts of unnecessary time from every Admin that might want to solve these time costs for their group or organisation Users.
I cannot think of a single reason why anyone would not want this to be just a basic standard features. It's not as if the world didn't already agree LDAP is a solution. Now we have to get every LDAP platform to agree to allow it to talk to every other LDAP support platform too it seems.
-
@fbartels Thanks - so far UCS is a long way from intuitive. I feel like I got invited around for dinner and pointed at the kitchen while everyone else already ate.
It seems strange to have to install an App for Lets Encrypt, as in that should just be a standard feature enabled for all to use or ignore.
I have a feeling we're going to have to start again with reimagine this VPS because guesswork setups and issues are costing way more time that expected.
The world really doesn't like solving the obvious needs in obvious ways.
Really appreciate the instructions as I'm tearing my hair out with now over a day on something that I really don't think should be this complicated.
It's like we have to deal with developers that think: "Well, we could make that possible, but since no-one has explicitly campaigned for it, lets just say its possible but not actually solve it, so everyone has to either learn everything we already know, or spend more time convincing us to make something obvious, then we might think about."
My only sanctuary in persevering with all this, is that with Microsoft, Google & AWS they'd also try and sell you some certified course nonsense as well before allowing you to play their specifically different ways.
@marcusquinn said in LDAP/AD Server:
so far UCS is a long way from intuitive
Yes, I can imagine if you have no experience with windows domain administration there are a lot of foreign concepts in ucs. Plus its a system that has evolved over more than a decade by now so it lacks a few more modern approaches that Cloudron serves very well.
On the other hand I always get too much already when only seeing a Wordpress login form

-
@fbartels Thanks - so far UCS is a long way from intuitive. I feel like I got invited around for dinner and pointed at the kitchen while everyone else already ate.
It seems strange to have to install an App for Lets Encrypt, as in that should just be a standard feature enabled for all to use or ignore.
I have a feeling we're going to have to start again with reimagine this VPS because guesswork setups and issues are costing way more time that expected.
The world really doesn't like solving the obvious needs in obvious ways.
Really appreciate the instructions as I'm tearing my hair out with now over a day on something that I really don't think should be this complicated.
It's like we have to deal with developers that think: "Well, we could make that possible, but since no-one has explicitly campaigned for it, lets just say its possible but not actually solve it, so everyone has to either learn everything we already know, or spend more time convincing us to make something obvious, then we might think about."
My only sanctuary in persevering with all this, is that with Microsoft, Google & AWS they'd also try and sell you some certified course nonsense as well before allowing you to play their specifically different ways.
@marcusquinn said in LDAP/AD Server:
@fbartels Thanks - so far UCS is a long way from intuitive. I feel like I got invited around for dinner and pointed at the kitchen while everyone else already ate.
A bit off topic but I love your analogies

-
@marcusquinn said in LDAP/AD Server:
so far UCS is a long way from intuitive
Yes, I can imagine if you have no experience with windows domain administration there are a lot of foreign concepts in ucs. Plus its a system that has evolved over more than a decade by now so it lacks a few more modern approaches that Cloudron serves very well.
On the other hand I always get too much already when only seeing a Wordpress login form

@fbartels I keep trying to forget my Windows years but it seems the rest of the world is still there

We'll keep plugging away at this. Considering all we're looking for is just one master LDAP server. It seems a ripe opportunity for Cloudron to be that. Having a whole other VPS, OS & Platform for a single feature is kinda inefficient, but then the other options all look like vendor-lockin options.
-
@friep2 As a fellow regular user, could I ask you to elaborate a bit on why it would be inappropriate to package up the "open-source / self-developed" apps to run inside Cloudron directly? This is an honest question, I'm quite curious about how different people perceive the limits of Cloudron. I'm sure you have considered many different options for deployment.
@infogulch to be fair i did not look too much into the process of wrapping up apps in cloudron. if it's quite easy and flexible that could be an alternative for us

Still, sometimes i guess it's just easier / more convenient to keep things separated and integrate via LDAP. E.g. in cases where you might not want to give people access to the cloudron server (which i suppose they'd need to deploy the app).
-
uff just having read the whole thread: i didn't want to open up a Pandoras box with my comment for anyone, especially @marcusquinn.
 Thanks for looking into it!!
Thanks for looking into it!!
it's definitely more a nice-to-have feature for our organisation, so its absence won't keep me from pursuing cloudron
-
uff just having read the whole thread: i didn't want to open up a Pandoras box with my comment for anyone, especially @marcusquinn.
 Thanks for looking into it!!
Thanks for looking into it!!
it's definitely more a nice-to-have feature for our organisation, so its absence won't keep me from pursuing cloudron
@friep2 haha, someone has to be the lucky person to start any thread.
Just happens to be one I need to get to a "once and for all" solution now as it's a PITA without, nothing more frustrating than time wasted that doesn't need to be.
Making progress with the UCS setup alternative, and will try and post a step-by-step guide once we've gathered all those good pointers and followed it all through to working.
-
OK, so we have Cloudron and Univention Corporate Server (UCS) connected and seemingly working.
A couple of questions:
- "Automatically create users when they login to Cloudron" - is this just creating Cloudron Users when someone tries to login that has a USC login/pass but not yet a Cloudron User?
- Is there any way to sync Cloudron Users upstream to UCS?
- Does this support SSO?
-
OK, so we have Cloudron and Univention Corporate Server (UCS) connected and seemingly working.
A couple of questions:
- "Automatically create users when they login to Cloudron" - is this just creating Cloudron Users when someone tries to login that has a USC login/pass but not yet a Cloudron User?
- Is there any way to sync Cloudron Users upstream to UCS?
- Does this support SSO?
- It's only creates users in Cloudron, if the user exists in UCS. This is where the self-service platform comes in.
- No. (not in my understanding of the external LDAP connection from Cloudron side).
- good question
 If you've tried it out, please share your wisdom with us.
If you've tried it out, please share your wisdom with us.
Attention:
- The allowed characters for UCS & Cloudron users are different. You can create UCS users which never allowed to login into Cloudron because of the character limitations in Cloudron. https://docs.cloudron.io/user-management/#valid-usernames
Sorry I never managed a kind of policy to disallow special characters on UCS. - The email address which Cloudron needs (without an email, the user doesn't exist) is labeled
primary email addresson UCS side.
-
OK, so we have Cloudron and Univention Corporate Server (UCS) connected and seemingly working.
A couple of questions:
- "Automatically create users when they login to Cloudron" - is this just creating Cloudron Users when someone tries to login that has a USC login/pass but not yet a Cloudron User?
- Is there any way to sync Cloudron Users upstream to UCS?
- Does this support SSO?
@marcusquinn said in LDAP/AD Server:
Does this support SSO?
That is why I suggested to run UCS in your local network. You could SSO with Kerberos from your workstation and then be directly signed into configured saml and oidc applications (and Kerberos of course as well). This only has two downsides:
- their sso clashes with their lets encrypt app, which requires manual work after the first certificate has been retrieved.
- this all does not touch Cloudron anymore, except you mod applications on Cloudron for one of the above auth methods
