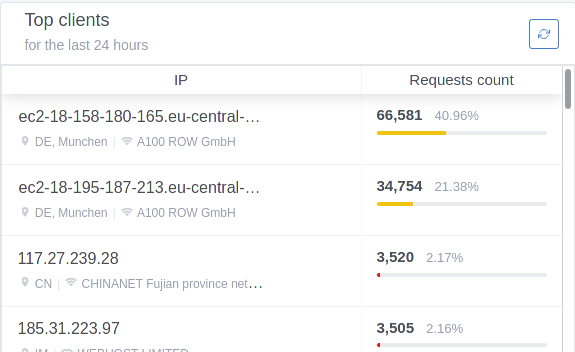
adguard on upcoming Cloudron v6 DDoS reflection/amplification
-
That’s why I suggested many many times to have Pi-Hole (preferred) together with a WireGuard VPN server. This app only on a VPS is dangerous!!!
-
But I would like to keep that feature

My own Adguard which I can use even while being on the go via mobile data.This could be usefull.
-
A background article on the DDoS problem can be found on the BSI website itself.
I have no idea what happens if we follow the
Solution
Disable recursion or limit recursion to trusted clients in the DNS server's configuration.But maybe it's a/the solution

-
A background article on the DDoS problem can be found on the BSI website itself.
I have no idea what happens if we follow the
Solution
Disable recursion or limit recursion to trusted clients in the DNS server's configuration.But maybe it's a/the solution

@luckow said in adguard on upcoming Cloudron v6 DDoS reflection/amplification:
I have no idea what happens if we follow the
Solution
Disable recursion or limit recursion to trusted clients in the DNS server's configuration.
But maybe it's a/the solutionIt is not a solution. It means the DNS server of the app would be forbidden to ask an upstream DNS server when it does not know a domain, which would basically make it useless

-
@luckow said in adguard on upcoming Cloudron v6 DDoS reflection/amplification:
I have no idea what happens if we follow the
Solution
Disable recursion or limit recursion to trusted clients in the DNS server's configuration.
But maybe it's a/the solutionIt is not a solution. It means the DNS server of the app would be forbidden to ask an upstream DNS server when it does not know a domain, which would basically make it useless

@mehdi thanks for the clarification
 In that case there is no easy solution for that problem. IMHO we only have a chance to use adguard on cloudron in a public infrastructure, if we only allow the use of adguard from inside the openvpn-app. That is my understanding of @imc67 pi-hole / wireguard vpn solution.
In that case there is no easy solution for that problem. IMHO we only have a chance to use adguard on cloudron in a public infrastructure, if we only allow the use of adguard from inside the openvpn-app. That is my understanding of @imc67 pi-hole / wireguard vpn solution. -
@brutalbirdie Wouldn't a raspberry pi with PiVPN and PiHole installed do the same thing for you?
@humptydumpty No, Pihole is installed locally on the pi attached to the local VPN adapter (wg0 if you're using wireguard). PiVPN internally handles DNS queries and is not publicly resolvable from the public IP/
Unless you install Pihole on your public facing adapter instead of your VPN adapter. Then you're in abit of trouble.....
-
I though ADGuard had an inbuilt feature to allow only whitelisted IP's through?
-
I agree we should have a big warning with information highlighting security issues and how to go about handling them. I will update the https://docs.cloudron.io/apps/adguard-home/#security section in the docs.
@girish I can help with this doc when you're read sir - I've got a PiHole on the public internet and simply block all requests at the router except requests from my IP address. If I'm not mistaken, we'll have some sort of control in 6 to whitelist/blacklist access by IP address to an app?
-
I though ADGuard had an inbuilt feature to allow only whitelisted IP's through?
@dylightful said in adguard on upcoming Cloudron v6 DDoS reflection/amplification:
I though ADGuard had an inbuilt feature to allow only whitelisted IP's through?
Indeed, I will put this in the docs and the POSTINSTALL.
-
@dylightful said in adguard on upcoming Cloudron v6 DDoS reflection/amplification:
I though ADGuard had an inbuilt feature to allow only whitelisted IP's through?
Indeed, I will put this in the docs and the POSTINSTALL.
-
@girish couldn't it just be limited to the VPN interface which you get once connected? That way it remains private and there's no issue with dynamic IPs from home.
@robi If I understand correctly, you are suggesting that we restrict the app to only private IPs by default. Maybe the IP blocks in https://en.wikipedia.org/wiki/Reserved_IP_addresses ? Thing is I would say the most common deployment of Cloudron is on a VPS and with that as the default a big chunk of people won't be able to use the app out of the box.
I think a good solution is to add a app level firewall to Cloudron. I think it's something we can easily add for next release.
-
@robi If I understand correctly, you are suggesting that we restrict the app to only private IPs by default. Maybe the IP blocks in https://en.wikipedia.org/wiki/Reserved_IP_addresses ? Thing is I would say the most common deployment of Cloudron is on a VPS and with that as the default a big chunk of people won't be able to use the app out of the box.
I think a good solution is to add a app level firewall to Cloudron. I think it's something we can easily add for next release.
@girish
Not what I said, but in effect yes.What I am suggesting is to limit it to an actual interface not an IP. Anything flowing through a VPN interface for example which is a higher abstraction.
Since private networks use RFC1918 addressing that's what ends up flowing through those interfaces. Hence the effect.
Having a by default secure install is the only option IMO.
Anyone installing it will need to configure it properly, be it for VPN access and network interfaces, or by going lower into the networking stack and using IP:port settings.It's also a question of liability for you, allowing deployment for DDoS or not.
Subsequent modification is the users responsibility.
Even if you had an app level firewall, how will it dynamically configure itself for a new client IP every hour? (there are ways but beyond the scope of this discussion)
-
I am reading up on what the upstream project recommends because IMO it's actually fairly easy to do an IP based rate limit in the app itself. There are several issues around this:
-
I am reading up on what the upstream project recommends because IMO it's actually fairly easy to do an IP based rate limit in the app itself. There are several issues around this:
@girish
Playing around with ADGuard today. The inbuilt IP limiter works great and correctly blocks amp attacks.Only issue i found was the ability to use DDNS hostnames as a whitelist for dynamic IP nets. CIDR works just aswell i guess...
-
@girish
Playing around with ADGuard today. The inbuilt IP limiter works great and correctly blocks amp attacks.Only issue i found was the ability to use DDNS hostnames as a whitelist for dynamic IP nets. CIDR works just aswell i guess...
@dylightful said in adguard on upcoming Cloudron v6 DDoS reflection/amplification:
Playing around with ADGuard today. The inbuilt IP limiter works great and correctly blocks amp attacks.
Do you mean the requests per second limit?
Which setting blocks amp attacks?Only issue i found was the ability to use DDNS hostnames as a whitelist for dynamic IP nets. CIDR works just aswell i guess...
I had an issue with this too, as I couldn't come up with a CIDR address that would exclude some of the abusing IPs without blocking my own (same network provider).
-
@dylightful said in adguard on upcoming Cloudron v6 DDoS reflection/amplification:
Playing around with ADGuard today. The inbuilt IP limiter works great and correctly blocks amp attacks.
Do you mean the requests per second limit?
Which setting blocks amp attacks?Only issue i found was the ability to use DDNS hostnames as a whitelist for dynamic IP nets. CIDR works just aswell i guess...
I had an issue with this too, as I couldn't come up with a CIDR address that would exclude some of the abusing IPs without blocking my own (same network provider).
@robi you might have to put it behind a firewall then and only allow internal - you could then have your servers vpn in to your box to query it (I do that for one of my friends).
There's another thread about making apps accessible only from OpenVPN - that would be a neat use case. -
@robi you might have to put it behind a firewall then and only allow internal - you could then have your servers vpn in to your box to query it (I do that for one of my friends).
There's another thread about making apps accessible only from OpenVPN - that would be a neat use case.Would that be OK to configure the firewall on the machine where cloudron is running? In the documentation says to not touch iptables/ufw and similar stuff, so I guess it's not a good idea. Yet, since this is a very serious matter of having AdGuard running wild out there, I would propose to have the app configure the firewall itself -- instead of relying to 3rd party firewalls -- and make this configurable (enable/disable).
Upon installation, it could ask you what you would like to do:
- Block port 53 - allow internal traffic only for AdGuard (recommended)
- Do not configure firewall.
WDYT?
-
Would that be OK to configure the firewall on the machine where cloudron is running? In the documentation says to not touch iptables/ufw and similar stuff, so I guess it's not a good idea. Yet, since this is a very serious matter of having AdGuard running wild out there, I would propose to have the app configure the firewall itself -- instead of relying to 3rd party firewalls -- and make this configurable (enable/disable).
Upon installation, it could ask you what you would like to do:
- Block port 53 - allow internal traffic only for AdGuard (recommended)
- Do not configure firewall.
WDYT?
-
@drpaneas did you see the docs at https://docs.cloudron.io/apps/adguard-home/#securing-installation already?
@nebulon yes of course I've read those. My proposal is to have cloudron blocking the port 53 during the installation automatically -- instead of asking the user to do it manually in the docs. In that way we make AdGuard installation more secure by default, instead of relying to the end user to take care of it.