Sharing custom SpamAssassin Rules
-
@andreasdueren Yeah, I see the limitation with that set up. Also applies to aliases. It would be nice to block an address when spammers get hold of it.
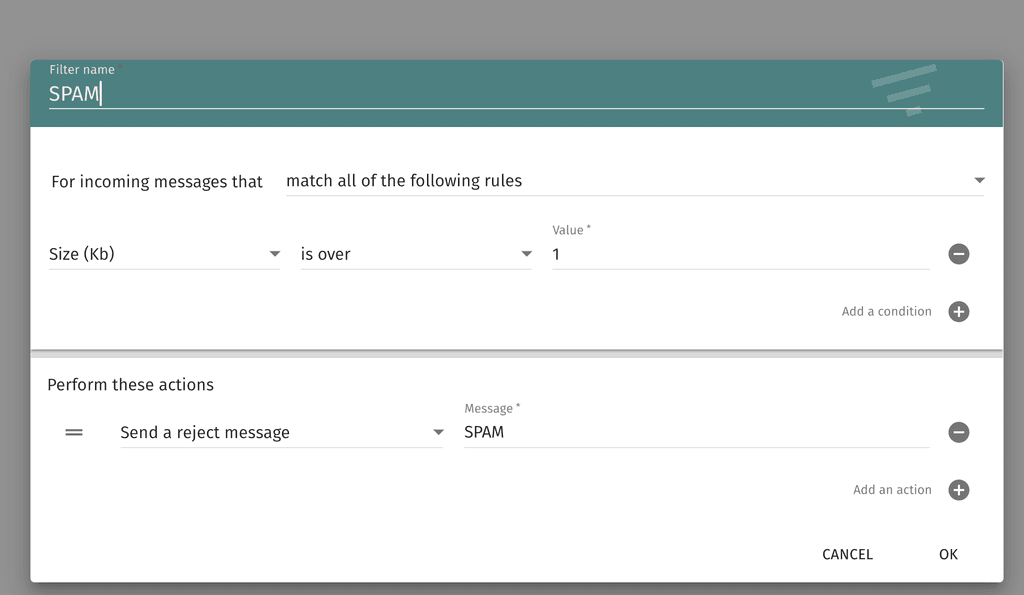
@humptydumpty Just checked, didn't work, reverted to the catch all. Enabling it and creating this filter did do the trick though.
-
I was just looking at using a "filter" in Roundcube. Similar end result.
Edit: Turns out I got a few of them set up for aliases, so it should work for catch-all addresses too.
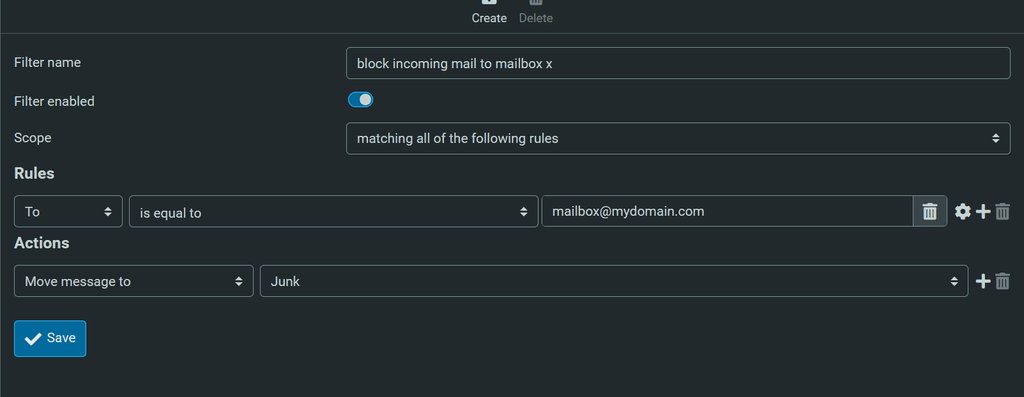
BTW, why use a catch-all instead of an alias/wildcard?
-
I was just looking at using a "filter" in Roundcube. Similar end result.
Edit: Turns out I got a few of them set up for aliases, so it should work for catch-all addresses too.

BTW, why use a catch-all instead of an alias/wildcard?
@humptydumpty Not my setup so don't ask me for why not alias lol
 What's the difference between wildcard and catch-all? On a sidenote: some spam might not fill in the "to". Not sure if this is checking for the header content or arriving address
What's the difference between wildcard and catch-all? On a sidenote: some spam might not fill in the "to". Not sure if this is checking for the header content or arriving address -
@humptydumpty Not my setup so don't ask me for why not alias lol
 What's the difference between wildcard and catch-all? On a sidenote: some spam might not fill in the "to". Not sure if this is checking for the header content or arriving address
What's the difference between wildcard and catch-all? On a sidenote: some spam might not fill in the "to". Not sure if this is checking for the header content or arriving address@andreasdueren said in Sharing custom SpamAssassin Rules:
Not sure if this is checking for the header content or arriving address
Good point. One way to find out

I've been transitioning away from aliases to wildcard, mostly for services that I wouldn't be sending mail from. My understanding is that anything to x@yourdomain.com will be fetched by the catch-all, so spammers send emails to see if you have a catch-all inbox or not. With the wildcard method, spammers need to target it specifically for it to work. For instance, you can set up something like:
*services@domain.com
netflixservices@domain.com
googleservices@domain.com
onetimepurchaseservices@domain.com
aldiservices@domain.com
etc..Use multiple wildcards:
*crapps@
*yourinitials@
*family@
*groups@and all of these would be "active" without you having to create it beforehand. It comes in handy when you need an email on the fly and want it to be identified with a specific service.
Edit: I've had my FedEx email address get compromised, but it was using a wildcard. In my FedEx account I updated my address by adding a number to the wildcard (fedex5services@domain.com). Then, I created a filter in roundcube for the old fedex address to send all incoming mail to the junk folder. I haven't seen a single address pass-through.
BTW, you can make wildcards less obvious (I believe in security thru obscurity) by abbreviating things, using initials, different languages, wordplay, etc.
-
@andreasdueren said in Sharing custom SpamAssassin Rules:
Not sure if this is checking for the header content or arriving address
Good point. One way to find out

I've been transitioning away from aliases to wildcard, mostly for services that I wouldn't be sending mail from. My understanding is that anything to x@yourdomain.com will be fetched by the catch-all, so spammers send emails to see if you have a catch-all inbox or not. With the wildcard method, spammers need to target it specifically for it to work. For instance, you can set up something like:
*services@domain.com
netflixservices@domain.com
googleservices@domain.com
onetimepurchaseservices@domain.com
aldiservices@domain.com
etc..Use multiple wildcards:
*crapps@
*yourinitials@
*family@
*groups@and all of these would be "active" without you having to create it beforehand. It comes in handy when you need an email on the fly and want it to be identified with a specific service.
Edit: I've had my FedEx email address get compromised, but it was using a wildcard. In my FedEx account I updated my address by adding a number to the wildcard (fedex5services@domain.com). Then, I created a filter in roundcube for the old fedex address to send all incoming mail to the junk folder. I haven't seen a single address pass-through.
BTW, you can make wildcards less obvious (I believe in security thru obscurity) by abbreviating things, using initials, different languages, wordplay, etc.
@humptydumpty Oh I didn't know you could use an Asterix for partial wildcards. That's a neat feature
-
@humptydumpty Oh I didn't know you could use an Asterix for partial wildcards. That's a neat feature
@andreasdueren That‘s what I use daily.
-
@humptydumpty Just checked, didn't work, reverted to the catch all. Enabling it and creating this filter did do the trick though.

@andreasdueren BTW catch-alls are being identified with several vendors these days: https://forum.cloudron.io/topic/10094/catch-all-mailboxes-are-being-identified-by-many-vendors-these-days
I haven’t read what they do with this information but it’s probably not to one‘s advantage -
@andreasdueren BTW catch-alls are being identified with several vendors these days: https://forum.cloudron.io/topic/10094/catch-all-mailboxes-are-being-identified-by-many-vendors-these-days
I haven’t read what they do with this information but it’s probably not to one‘s advantage@necrevistonnezr Yes I know but I have users who will insist on this. And partial wildcards are still better than complete ones
-
Okay everyone... I've spent the past month really fine-tuning the SpamAssassin rules (especially after SpamAssassin was upgraded to 4.0 with Cloudron 8.3), and it seems to be working quite well for me. Spam filtering is never perfect, but it has improved a lot since the last time I took a look at the rules. The list is much longer now, and I added many more rules along with some additional lists for extra checks too.
If you want to use Abusix (which I've found to be very reliable), then you'll need a free API key, and can replace <API_KEY> in the list below with your own.
As always, your own mileage may vary, but this should be an effective SpamAssassin rule set to use. Good luck.

# ============================ # Allowlist / Blocklist Rules # ============================ score USER_IN_BLOCKLIST 50.0 score USER_IN_ALL_SPAM_TO -50.0 score USER_IN_MORE_SPAM_TO -10.0 score USER_IN_WELCOMELIST -50.0 ## Block specific recipients/senders blocklist_from <EMAIL> ## Allowlist specific recipients/senders welcomelist_from <EMAIL> # ============================ # Bayesian Filtering (BAYES) # ============================ bayes_auto_learn 1 bayes_auto_learn_threshold_nonspam -4.0 bayes_auto_learn_threshold_spam 12.0 score BAYES_00 -6.0 score BAYES_05 -4.0 score BAYES_20 1.5 score BAYES_40 2.5 score BAYES_50 3.25 score BAYES_60 3.75 score BAYES_80 4.25 score BAYES_95 5.5 score BAYES_99 7.0 score BAYES_999 7.5 # ============================ # DNS-based Blocklists (DNSBL) # ============================ ## DNS Blocklists score RCVD_IN_BL_SPAMCOP_NET 2.5 score RCVD_IN_MSPIKE_BL 0.0 score RCVD_IN_MSPIKE_L2 1.0 score RCVD_IN_MSPIKE_L3 1.5 score RCVD_IN_MSPIKE_L4 3.5 score RCVD_IN_MSPIKE_L5 5.0 score RCVD_IN_MSPIKE_ZBI 4.0 score RCVD_IN_PBL 3.5 score RCVD_IN_SBL 5.0 score RCVD_IN_SBL_CSS 4.0 score RCVD_IN_VALIDITY_RPBL 1.5 score RCVD_IN_XBL 6.0 score RCVD_IN_ZEN_BLOCKED 0.0 score RCVD_IN_ZEN_BLOCKED_OPENDNS 0.0 ## DNS Whitelists score RCVD_IN_DNSWL_BLOCKED 0.0 score RCVD_IN_DNSWL_HI -6.0 score RCVD_IN_DNSWL_LOW -2.5 score RCVD_IN_DNSWL_MED -4.5 score RCVD_IN_DNSWL_NONE 0.0 score RCVD_IN_MSPIKE_H2 -1.0 score RCVD_IN_MSPIKE_H3 -1.5 score RCVD_IN_MSPIKE_H4 -3.5 score RCVD_IN_MSPIKE_H5 -5.0 score RCVD_IN_MSPIKE_WL 0.0 # ============================ # URI Blocklists (URIBL) # ============================ score URIBL_ABUSE_SURBL 6.0 score URIBL_BLACK 7.0 score URIBL_CR_SURBL 3.5 score URIBL_CSS 3.0 score URIBL_CSS_A 3.0 score URIBL_DBL_ABUSE_BOTCC 5.5 score URIBL_DBL_ABUSE_MALW 5.5 score URIBL_DBL_ABUSE_PHISH 5.5 score URIBL_DBL_ABUSE_REDIR 2.0 score URIBL_DBL_ABUSE_SPAM 5.5 score URIBL_DBL_BLOCKED 0.0 score URIBL_DBL_BLOCKED_OPENDNS 0.0 score URIBL_DBL_BOTNETCC 5.5 score URIBL_DBL_ERROR 0.0 score URIBL_DBL_MALWARE 5.5 score URIBL_DBL_PHISH 5.5 score URIBL_DBL_SPAM 5.5 score URIBL_GREY 0.5 score URIBL_MW_SURBL 5.0 score URIBL_PH_SURBL 5.0 score URIBL_RED 2.0 score URIBL_RHS_DOB 2.0 score URIBL_SBL 4.0 score URIBL_SBL_A 3.0 score URIBL_ZEN_BLOCKED 0.0 score URIBL_ZEN_BLOCKED_OPENDNS 0.0 # ============================ # Email Authentication (SPF/DKIM/ARC) # ============================ ## DKIM score DKIM_INVALID 2.0 score DKIM_ADSP_ALL 2.0 score DKIM_ADSP_CUSTOM_MED 1.5 score DKIM_ADSP_NXDOMAIN 4.5 score DKIM_SIGNED 0.0 score DKIM_VALID 0.0 score DKIM_VALID_AU 0.0 score DKIM_VALID_EF 0.0 score DKIM_VERIFIED 0.0 score DKIMWL_BL 3.0 score DKIMWL_WL_HIGH -6.0 score DKIMWL_WL_MED -4.0 score DKIMWL_WL_MEDHI -4.5 score USER_IN_DEF_DKIM_WL -6.0 ## SPF score FORGED_SPF_HELO 4.0 score SPF_FAIL 4.0 score SPF_HELO_FAIL 2.5 score SPF_HELO_NEUTRAL 1.0 score SPF_HELO_NONE 0.25 score SPF_HELO_PASS -1.0 score SPF_HELO_SOFTFAIL 4.0 score SPF_NEUTRAL 0.0 score SPF_NONE 1.0 score SPF_PASS -1.0 score SPF_SOFTFAIL 1.5 score T_SPF_PERMERROR 2.0 score T_SPF_TEMPERROR 0.0 score USER_IN_DEF_SPF_WL -6.0 ## ARC score ARC_INVALID 2.0 score ARC_SIGNED 0.0 score ARC_VALID -0.5 # ============================ # HTML & MIME Structure Rules # ============================ score HTML_FONT_LOW_CONTRAST 0.0 score HTML_FONT_SIZE_LARGE 2.0 score HTML_FONT_TINY_NORDNS 0.0 score HTML_IMAGE_ONLY_04 1.25 score HTML_IMAGE_ONLY_08 1.25 score HTML_IMAGE_ONLY_12 1.25 score HTML_IMAGE_ONLY_16 1.25 score HTML_IMAGE_ONLY_20 1.25 score HTML_IMAGE_ONLY_24 1.25 score HTML_IMAGE_ONLY_28 1.25 score HTML_IMAGE_ONLY_32 1.25 score HTML_MESSAGE 0.0 score HTML_MIME_NO_HTML_TAG 0.5 score HTML_OBFUSCATE_05_10 0.5 score HTML_OBFUSCATE_10_20 1.0 score HTML_OBFUSCATE_20_30 2.0 score HTML_OBFUSCATE_30_40 2.5 score HTML_OBFUSCATE_50_60 3.0 score HTML_OBFUSCATE_70_80 3.5 score HTML_OBFUSCATE_90_100 4.0 score HTML_SHORT_LINK_IMG_1 2.0 score HTML_SHORT_LINK_IMG_2 3.0 score HTML_SHORT_LINK_IMG_3 3.0 score MIME_HTML_MOSTLY 0.0 score MIME_HTML_ONLY 0.0 score MPART_ALT_DIFF 0.5 score MPART_ALT_DIFF_COUNT 0.5 # ============================ # Header / Envelope Heuristics # ============================ score HEADER_FROM_DIFFERENT_DOMAINS 2.0 score MISSING_DATE 2.5 score MISSING_FROM 2.0 score MISSING_HEADERS 2.5 score MISSING_MID 1.0 score MISSING_SUBJECT 1.0 score MSGID_OUTLOOK_INVALID 4.0 score MISSING_HB_SEP 2.0 score TO_NO_BRKTS_FROM_MSSP 1.5 score REPLYTO_WITHOUT_TO_CC 2.5 # ============================ # Freemail & Identity Rules # ============================ score FREEMAIL_ENVFROM_END_DIGIT 1.0 score FREEMAIL_FORGED_REPLYTO 2.25 score FREEMAIL_FROM 0.0 score FREEMAIL_REPLY 0.5 score FREEMAIL_REPLYTO 2.0 score FREEMAIL_REPLYTO_END_DIGIT 0.0 score FROM_LOCAL_DIGITS 1.75 score FROM_EXCESS_BASE64 2.5 score FROM_FMBLA_NEWDOM 2.5 score FROM_FMBLA_NEWDOM14 3.0 score FROM_FMBLA_NEWDOM28 2.5 score FROM_SUSPICIOUS_NTLD 2.0 score FORGED_GMAIL_RCVD 3.0 score FORGED_MUA_OUTLOOK 3.0 score FORGED_YAHOO_RCVD 3.0 # ============================ # Scam, Phishing & Social Engineering # ============================ score ADVANCE_FEE_2 3.0 score ADVANCE_FEE_2_NEW_MONEY 3.0 score ADVANCE_FEE_2_NEW_FORM 3.0 score ADVANCE_FEE_3 3.0 score ADVANCE_FEE_3_NEW 3.0 score ADVANCE_FEE_3_NEW_MONEY 3.0 score ADVANCE_FEE_3_NEW_FORM 3.0 score ADVANCE_FEE_4_NEW 3.0 score ADVANCE_FEE_5_NEW 3.0 score ADVANCE_FEE_5_NEW_FRM_MNY 3.0 score ADVANCE_FEE_5_NEW_MONEY 3.0 score BILLION_DOLLARS 1.0 score DEAR_FRIEND 1.5 score LOTS_OF_MONEY 0.0 score UNCLAIMED_MONEY 4.0 score URG_BIZ 1.5 score FUZZY_CLICK_HERE 1.5 score FUZZY_CREDIT 2.0 score FUZZY_IMPORTANT 2.0 score FUZZY_SECURITY 2.25 score FUZZY_UNSUBSCRIBE 1.0 score SUBJ_AS_SEEN 0.75 score SUBJ_DOLLARS 0.25 score SUBJ_YOUR_DEBT 2.5 score SUBJ_YOUR_FAMILY 0.75 # ============================ # Transport / Network Reputation Rules # ============================ score NO_RDNS_DOTCOM_HELO 3.0 score RDNS_DYNAMIC 3.5 score RDNS_LOCALHOST 3.5 score RDNS_NONE 2.25 score RCVD_HELO_IP_MISMATCH 1.75 score RCVD_ILLEGAL_IP 4.0 score PDS_BAD_THREAD_QP_64 1.5 score TBIRD_SUSP_MIME_BDRY 2.5 score SPAMMY_XMAILER 2.75 score KHOP_HELO_FCRDNS -0.5 score HELO_DYNAMIC_IPADDR 2.0 score HELO_DYNAMIC_SPLIT_IP 2.0 score UNPARSEABLE_RELAY 0.0 # ============================ # URI & Link Obfuscation # ============================ score URI_HEX 2.5 score URI_NO_WWW_BIZ_CGI 2.5 score URI_NO_WWW_INFO_CGI 2.5 score URI_OBFU_WWW 3.0 score URI_TRUNCATED 2.5 score HTTPS_HTTP_MISMATCH 0.25 score WEIRD_PORT 4.5 # ============================ # Miscellaneous Heuristics & Content Triggers # ============================ score ENV_AND_HDR_SPF_MATCH -4.0 score DATE_IN_FUTURE_06_12 2.25 score DATE_IN_PAST_03_06 2.25 score DATE_IN_PAST_06_12 2.25 score PLING_QUERY 1.0 score SHOPIFY_IMG_NOT_RCVD_SFY 0.75 score T_FILL_THIS_FORM_SHORT 0.25 score T_REMOTE_IMAGE 0.25 score STOX_REPLY_TYPE 2.0 score STOX_REPLY_TYPE_WITHOUT_QUOTES 3.0 score SUSPICIOUS_RECIPS 2.5 # ============================ # Spam Eating Monkey DNSBL lists # ============================ header RCVD_IN_SEM_BACKSCATTER eval:check_rbl('sembackscatter-lastexternal', 'backscatter.spameatingmonkey.net') describe RCVD_IN_SEM_BACKSCATTER Received from an IP listed by Spam Eating Monkey Backscatter list tflags RCVD_IN_SEM_BACKSCATTER net score RCVD_IN_SEM_BACKSCATTER 3.0 header RCVD_IN_SEM_BLACK eval:check_rbl('semblack-lastexternal', 'bl.spameatingmonkey.net') tflags RCVD_IN_SEM_BLACK net describe RCVD_IN_SEM_BLACK Received from an IP listed by Spam Eating Monkey Blocklist score RCVD_IN_SEM_BLACK 3.0 header RCVD_IN_SEM_NETBLACK eval:check_rbl('semnetblack-lastexternal', 'netbl.spameatingmonkey.net') tflags RCVD_IN_SEM_NETBLACK net describe RCVD_IN_SEM_NETBLACK Received from an IP listed by Spam Eating Monkeys Network Blocklist score RCVD_IN_SEM_NETBLACK 1.5 urirhssub SEM_FRESH30 fresh30.spameatingmonkey.net. A 2 body SEM_FRESH30 eval:check_uridnsbl('SEM_FRESH30') describe SEM_FRESH30 Contains a domain registered less than 30 days ago tflags SEM_FRESH30 net score SEM_FRESH30 3.0 urirhssub SEM_URI_BLACK uribl.spameatingmonkey.net. A 2 body SEM_URI_BLACK eval:check_uridnsbl('SEM_URI') describe SEM_URI_BLACK Contains a URI listed by Spam Eating Monkeys URI Blocklist tflags SEM_URI_BLACK net score SEM_URI_BLACK 3.5 # ============================ # JunkEmailFilter HostKarma DNSBL & DNSWL # ============================ header __RCVD_IN_HOSTKARMA eval:check_rbl('hostkarma', 'hostkarma.junkemailfilter.com.') describe __RCVD_IN_HOSTKARMA Sender listed in JunkEmailFilter tflags __RCVD_IN_HOSTKARMA net header RCVD_IN_HOSTKARMA_W eval:check_rbl_sub('hostkarma','127.0.0.1') describe RCVD_IN_HOSTKARMA_W Sender listed in HOSTKARMA-WHITE tflags RCVD_IN_HOSTKARMA_W net nice score RCVD_IN_HOSTKARMA_W -3.5 header RCVD_IN_HOSTKARMA_BL eval:check_rbl_sub('hostkarma','127.0.0.2') describe RCVD_IN_HOSTKARMA_BL Sender listed in HOSTKARMA-BLACK tflags RCVD_IN_HOSTKARMA_BL net score RCVD_IN_HOSTKARMA_BL 3.0 header RCVD_IN_HOSTKARMA_BR eval:check_rbl_sub('hostkarma','127.0.0.4') describe RCVD_IN_HOSTKARMA_BR Sender listed in HOSTKARMA-BROWN tflags RCVD_IN_HOSTKARMA_BR net score RCVD_IN_HOSTKARMA_BR 1.25 # ============================ # SpamRATS DNSBL # ============================ header __RCVD_IN_SPAMRATS eval:check_rbl('spamrats', 'all.spamrats.com.') describe __RCVD_IN_SPAMRATS SPAMRATS: sender is listed in SpamRATS tflags __RCVD_IN_SPAMRATS net reuse __RCVD_IN_SPAMRATS header RCVD_IN_SPAMRATS_DYNA eval:check_rbl_sub('spamrats','127.0.0.36') describe RCVD_IN_SPAMRATS_DYNA RATS-Dyna: sent directly from dynamic IP address tflags RCVD_IN_SPAMRATS_DYNA net reuse RCVD_IN_SPAMRATS_DYNA score RCVD_IN_SPAMRATS_DYNA 2.25 header RCVD_IN_SPAMRATS_NOPTR eval:check_rbl_sub('spamrats','127.0.0.37') describe RCVD_IN_SPAMRATS_NOPTR RATS-NoPtr: sender has no reverse DNS tflags RCVD_IN_SPAMRATS_NOPTR net reuse RCVD_IN_SPAMRATS_NOPTR score RCVD_IN_SPAMRATS_NOPTR 2.5 header RCVD_IN_SPAMRATS_SPAM eval:check_rbl_sub('spamrats','127.0.0.38') describe RCVD_IN_SPAMRATS_SPAM RATS-Spam: sender is a spam source tflags RCVD_IN_SPAMRATS_SPAM net reuse RCVD_IN_SPAMRATS_SPAM score RCVD_IN_SPAMRATS_SPAM 5.5 # ============================ # UCEPROTECT # ============================ header RCVD_IN_UCEPROTECT_LEVEL_1 eval:check_rbl('uceprotect1', 'dnsbl-1.uceprotect.net.') describe RCVD_IN_UCEPROTECT_LEVEL_1 Sender IP listed in UCEPROTECT Level 1 tflags RCVD_IN_UCEPROTECT_LEVEL_1 net score RCVD_IN_UCEPROTECT_LEVEL_1 4.0 header RCVD_IN_UCEPROTECT_LEVEL_2 eval:check_rbl('uceprotect2', 'dnsbl-2.uceprotect.net.') describe RCVD_IN_UCEPROTECT_LEVEL_2 Sender IP listed in UCEPROTECT Level 2 tflags RCVD_IN_UCEPROTECT_LEVEL_2 net score RCVD_IN_UCEPROTECT_LEVEL_2 1.25 # ============================ # Abusix Guardian Mail Relay # ============================ header __RCVD_IN_ABUSIX eval:check_rbl('abusix', '<API_KEY>.combined.mail.abusix.zone.') describe __RCVD_IN_ABUSIX Received via a relay in Abusix Guardian Mail tflags __RCVD_IN_ABUSIX net header RCVD_IN_ABUSIX_BLACK eval:check_rbl_sub('abusix', '^127\.0\.0\.(?:[23]|200)$') describe RCVD_IN_ABUSIX_BLACK Received via a relay in Abusix Guardian Mail Black tflags RCVD_IN_ABUSIX_BLACK net score RCVD_IN_ABUSIX_BLACK 5.5 header RCVD_IN_ABUSIX_EXPLOIT eval:check_rbl_sub('abusix', '127.0.0.4') describe RCVD_IN_ABUSIX_EXPLOIT Received via a relay in Abusix Guardian Mail Exploit tflags RCVD_IN_ABUSIX_EXPLOIT net score RCVD_IN_ABUSIX_EXPLOIT 6.0 header RCVD_IN_ABUSIX_DYN eval:check_rbl('abusix_dyn', '<API_KEY>.combined.mail.abusix.zone.', '^127\.0\.0\.1[12]$') describe RCVD_IN_ABUSIX_DYN Received via a relay in Abusix Guardian Mail Dynamic tflags RCVD_IN_ABUSIX_DYN net score RCVD_IN_ABUSIX_DYN 1.5 header RCVD_IN_ABUSIX_WHITE eval:check_rbl('abusix_white', '<API_KEY>.combined.mail.abusix.zone.', '127.0.2.1') describe RCVD_IN_ABUSIX_WHITE Received via a relay in Abusix Guardian Mail White tflags RCVD_IN_ABUSIX_WHITE nice net score RCVD_IN_ABUSIX_WHITE -1.5 urirhsbl URIBL_ABUSIX_DBLACK <API_KEY>.dblack.mail.abusix.zone. A body URIBL_ABUSIX_DBLACK eval:check_uridnsbl('URIBL_ABUSIX_DBLACK') describe URIBL_ABUSIX_DBLACK Contains a spam URL listed in the Abusix domain blocklist tflags URIBL_ABUSIX_DBLACK net score URIBL_ABUSIX_DBLACK 6.0 urirhssub URIBL_ABUSIX_WHITE <API_KEY>.white.mail.abusix.zone. A 127.0.2.1 body URIBL_ABUSIX_WHITE eval:check_uridnsbl('URIBL_ABUSIX_WHITE') describe URIBL_ABUSIX_WHITE Contains a domain listed in the Abusix domain whitelist tflags URIBL_ABUSIX_WHITE nice net score URIBL_ABUSIX_WHITE -0.25 # ============================ # Ascams RBLs (IP Reputation) # ============================ header RCVD_IN_ASCAMS_BLOCK eval:check_rbl('ascams_block', 'block.ascams.com.') describe RCVD_IN_ASCAMS_BLOCK Sender listed in Ascams Block RBL tflags RCVD_IN_ASCAMS_BLOCK net score RCVD_IN_ASCAMS_BLOCK 1.25 header RCVD_IN_ASCAMS_DROP eval:check_rbl('ascams_white', 'dnsbl.ascams.com.') describe RCVD_IN_ASCAMS_DROP Sender listed in Ascams DROP list tflags RCVD_IN_ASCAMS_DROP nice net score RCVD_IN_ASCAMS_DROP 3.0 # ============================ # DroneBL DNSBL # ============================ header RCVD_IN_DRONEBL eval:check_rbl('dronebl', 'dnsbl.dronebl.org.') describe RCVD_IN_DRONEBL Sender listed in DroneBL (suspected bot/malware) tflags RCVD_IN_DRONEBL net score RCVD_IN_DRONEBL 3.0 # ============================ # GBUDB Truncate DNSBL # ============================ header RCVD_IN_GBUDB_TRUNCATE eval:check_rbl('gbudb', 'truncate.gbudb.net.') describe RCVD_IN_GBUDB_TRUNCATE Sender listed in GBUDB Truncate tflags RCVD_IN_GBUDB_TRUNCATE net score RCVD_IN_GBUDB_TRUNCATE 4.0 # ============================ # Usenix S5H # ============================ header RCVD_IN_S5H_BL eval:check_rbl_txt('s5hbl', 'all.s5h.net.') describe RCVD_IN_S5H_BL Listed at all.s5h.net tflags RCVD_IN_S5H_BL net score RCVD_IN_S5H_BL 0.5 # ============================ # Backscatterer.org # ============================ header RCVD_IN_BACKSCATTERER eval:check_rbl('backscatterer', 'ips.backscatterer.org.') describe RCVD_IN_BACKSCATTERER IP listed in Backscatterer (backscatter spam) tflags RCVD_IN_BACKSCATTERER net score RCVD_IN_BACKSCATTERER 3.5 -
Okay everyone... I've spent the past month really fine-tuning the SpamAssassin rules (especially after SpamAssassin was upgraded to 4.0 with Cloudron 8.3), and it seems to be working quite well for me. Spam filtering is never perfect, but it has improved a lot since the last time I took a look at the rules. The list is much longer now, and I added many more rules along with some additional lists for extra checks too.
If you want to use Abusix (which I've found to be very reliable), then you'll need a free API key, and can replace <API_KEY> in the list below with your own.
As always, your own mileage may vary, but this should be an effective SpamAssassin rule set to use. Good luck.

# ============================ # Allowlist / Blocklist Rules # ============================ score USER_IN_BLOCKLIST 50.0 score USER_IN_ALL_SPAM_TO -50.0 score USER_IN_MORE_SPAM_TO -10.0 score USER_IN_WELCOMELIST -50.0 ## Block specific recipients/senders blocklist_from <EMAIL> ## Allowlist specific recipients/senders welcomelist_from <EMAIL> # ============================ # Bayesian Filtering (BAYES) # ============================ bayes_auto_learn 1 bayes_auto_learn_threshold_nonspam -4.0 bayes_auto_learn_threshold_spam 12.0 score BAYES_00 -6.0 score BAYES_05 -4.0 score BAYES_20 1.5 score BAYES_40 2.5 score BAYES_50 3.25 score BAYES_60 3.75 score BAYES_80 4.25 score BAYES_95 5.5 score BAYES_99 7.0 score BAYES_999 7.5 # ============================ # DNS-based Blocklists (DNSBL) # ============================ ## DNS Blocklists score RCVD_IN_BL_SPAMCOP_NET 2.5 score RCVD_IN_MSPIKE_BL 0.0 score RCVD_IN_MSPIKE_L2 1.0 score RCVD_IN_MSPIKE_L3 1.5 score RCVD_IN_MSPIKE_L4 3.5 score RCVD_IN_MSPIKE_L5 5.0 score RCVD_IN_MSPIKE_ZBI 4.0 score RCVD_IN_PBL 3.5 score RCVD_IN_SBL 5.0 score RCVD_IN_SBL_CSS 4.0 score RCVD_IN_VALIDITY_RPBL 1.5 score RCVD_IN_XBL 6.0 score RCVD_IN_ZEN_BLOCKED 0.0 score RCVD_IN_ZEN_BLOCKED_OPENDNS 0.0 ## DNS Whitelists score RCVD_IN_DNSWL_BLOCKED 0.0 score RCVD_IN_DNSWL_HI -6.0 score RCVD_IN_DNSWL_LOW -2.5 score RCVD_IN_DNSWL_MED -4.5 score RCVD_IN_DNSWL_NONE 0.0 score RCVD_IN_MSPIKE_H2 -1.0 score RCVD_IN_MSPIKE_H3 -1.5 score RCVD_IN_MSPIKE_H4 -3.5 score RCVD_IN_MSPIKE_H5 -5.0 score RCVD_IN_MSPIKE_WL 0.0 # ============================ # URI Blocklists (URIBL) # ============================ score URIBL_ABUSE_SURBL 6.0 score URIBL_BLACK 7.0 score URIBL_CR_SURBL 3.5 score URIBL_CSS 3.0 score URIBL_CSS_A 3.0 score URIBL_DBL_ABUSE_BOTCC 5.5 score URIBL_DBL_ABUSE_MALW 5.5 score URIBL_DBL_ABUSE_PHISH 5.5 score URIBL_DBL_ABUSE_REDIR 2.0 score URIBL_DBL_ABUSE_SPAM 5.5 score URIBL_DBL_BLOCKED 0.0 score URIBL_DBL_BLOCKED_OPENDNS 0.0 score URIBL_DBL_BOTNETCC 5.5 score URIBL_DBL_ERROR 0.0 score URIBL_DBL_MALWARE 5.5 score URIBL_DBL_PHISH 5.5 score URIBL_DBL_SPAM 5.5 score URIBL_GREY 0.5 score URIBL_MW_SURBL 5.0 score URIBL_PH_SURBL 5.0 score URIBL_RED 2.0 score URIBL_RHS_DOB 2.0 score URIBL_SBL 4.0 score URIBL_SBL_A 3.0 score URIBL_ZEN_BLOCKED 0.0 score URIBL_ZEN_BLOCKED_OPENDNS 0.0 # ============================ # Email Authentication (SPF/DKIM/ARC) # ============================ ## DKIM score DKIM_INVALID 2.0 score DKIM_ADSP_ALL 2.0 score DKIM_ADSP_CUSTOM_MED 1.5 score DKIM_ADSP_NXDOMAIN 4.5 score DKIM_SIGNED 0.0 score DKIM_VALID 0.0 score DKIM_VALID_AU 0.0 score DKIM_VALID_EF 0.0 score DKIM_VERIFIED 0.0 score DKIMWL_BL 3.0 score DKIMWL_WL_HIGH -6.0 score DKIMWL_WL_MED -4.0 score DKIMWL_WL_MEDHI -4.5 score USER_IN_DEF_DKIM_WL -6.0 ## SPF score FORGED_SPF_HELO 4.0 score SPF_FAIL 4.0 score SPF_HELO_FAIL 2.5 score SPF_HELO_NEUTRAL 1.0 score SPF_HELO_NONE 0.25 score SPF_HELO_PASS -1.0 score SPF_HELO_SOFTFAIL 4.0 score SPF_NEUTRAL 0.0 score SPF_NONE 1.0 score SPF_PASS -1.0 score SPF_SOFTFAIL 1.5 score T_SPF_PERMERROR 2.0 score T_SPF_TEMPERROR 0.0 score USER_IN_DEF_SPF_WL -6.0 ## ARC score ARC_INVALID 2.0 score ARC_SIGNED 0.0 score ARC_VALID -0.5 # ============================ # HTML & MIME Structure Rules # ============================ score HTML_FONT_LOW_CONTRAST 0.0 score HTML_FONT_SIZE_LARGE 2.0 score HTML_FONT_TINY_NORDNS 0.0 score HTML_IMAGE_ONLY_04 1.25 score HTML_IMAGE_ONLY_08 1.25 score HTML_IMAGE_ONLY_12 1.25 score HTML_IMAGE_ONLY_16 1.25 score HTML_IMAGE_ONLY_20 1.25 score HTML_IMAGE_ONLY_24 1.25 score HTML_IMAGE_ONLY_28 1.25 score HTML_IMAGE_ONLY_32 1.25 score HTML_MESSAGE 0.0 score HTML_MIME_NO_HTML_TAG 0.5 score HTML_OBFUSCATE_05_10 0.5 score HTML_OBFUSCATE_10_20 1.0 score HTML_OBFUSCATE_20_30 2.0 score HTML_OBFUSCATE_30_40 2.5 score HTML_OBFUSCATE_50_60 3.0 score HTML_OBFUSCATE_70_80 3.5 score HTML_OBFUSCATE_90_100 4.0 score HTML_SHORT_LINK_IMG_1 2.0 score HTML_SHORT_LINK_IMG_2 3.0 score HTML_SHORT_LINK_IMG_3 3.0 score MIME_HTML_MOSTLY 0.0 score MIME_HTML_ONLY 0.0 score MPART_ALT_DIFF 0.5 score MPART_ALT_DIFF_COUNT 0.5 # ============================ # Header / Envelope Heuristics # ============================ score HEADER_FROM_DIFFERENT_DOMAINS 2.0 score MISSING_DATE 2.5 score MISSING_FROM 2.0 score MISSING_HEADERS 2.5 score MISSING_MID 1.0 score MISSING_SUBJECT 1.0 score MSGID_OUTLOOK_INVALID 4.0 score MISSING_HB_SEP 2.0 score TO_NO_BRKTS_FROM_MSSP 1.5 score REPLYTO_WITHOUT_TO_CC 2.5 # ============================ # Freemail & Identity Rules # ============================ score FREEMAIL_ENVFROM_END_DIGIT 1.0 score FREEMAIL_FORGED_REPLYTO 2.25 score FREEMAIL_FROM 0.0 score FREEMAIL_REPLY 0.5 score FREEMAIL_REPLYTO 2.0 score FREEMAIL_REPLYTO_END_DIGIT 0.0 score FROM_LOCAL_DIGITS 1.75 score FROM_EXCESS_BASE64 2.5 score FROM_FMBLA_NEWDOM 2.5 score FROM_FMBLA_NEWDOM14 3.0 score FROM_FMBLA_NEWDOM28 2.5 score FROM_SUSPICIOUS_NTLD 2.0 score FORGED_GMAIL_RCVD 3.0 score FORGED_MUA_OUTLOOK 3.0 score FORGED_YAHOO_RCVD 3.0 # ============================ # Scam, Phishing & Social Engineering # ============================ score ADVANCE_FEE_2 3.0 score ADVANCE_FEE_2_NEW_MONEY 3.0 score ADVANCE_FEE_2_NEW_FORM 3.0 score ADVANCE_FEE_3 3.0 score ADVANCE_FEE_3_NEW 3.0 score ADVANCE_FEE_3_NEW_MONEY 3.0 score ADVANCE_FEE_3_NEW_FORM 3.0 score ADVANCE_FEE_4_NEW 3.0 score ADVANCE_FEE_5_NEW 3.0 score ADVANCE_FEE_5_NEW_FRM_MNY 3.0 score ADVANCE_FEE_5_NEW_MONEY 3.0 score BILLION_DOLLARS 1.0 score DEAR_FRIEND 1.5 score LOTS_OF_MONEY 0.0 score UNCLAIMED_MONEY 4.0 score URG_BIZ 1.5 score FUZZY_CLICK_HERE 1.5 score FUZZY_CREDIT 2.0 score FUZZY_IMPORTANT 2.0 score FUZZY_SECURITY 2.25 score FUZZY_UNSUBSCRIBE 1.0 score SUBJ_AS_SEEN 0.75 score SUBJ_DOLLARS 0.25 score SUBJ_YOUR_DEBT 2.5 score SUBJ_YOUR_FAMILY 0.75 # ============================ # Transport / Network Reputation Rules # ============================ score NO_RDNS_DOTCOM_HELO 3.0 score RDNS_DYNAMIC 3.5 score RDNS_LOCALHOST 3.5 score RDNS_NONE 2.25 score RCVD_HELO_IP_MISMATCH 1.75 score RCVD_ILLEGAL_IP 4.0 score PDS_BAD_THREAD_QP_64 1.5 score TBIRD_SUSP_MIME_BDRY 2.5 score SPAMMY_XMAILER 2.75 score KHOP_HELO_FCRDNS -0.5 score HELO_DYNAMIC_IPADDR 2.0 score HELO_DYNAMIC_SPLIT_IP 2.0 score UNPARSEABLE_RELAY 0.0 # ============================ # URI & Link Obfuscation # ============================ score URI_HEX 2.5 score URI_NO_WWW_BIZ_CGI 2.5 score URI_NO_WWW_INFO_CGI 2.5 score URI_OBFU_WWW 3.0 score URI_TRUNCATED 2.5 score HTTPS_HTTP_MISMATCH 0.25 score WEIRD_PORT 4.5 # ============================ # Miscellaneous Heuristics & Content Triggers # ============================ score ENV_AND_HDR_SPF_MATCH -4.0 score DATE_IN_FUTURE_06_12 2.25 score DATE_IN_PAST_03_06 2.25 score DATE_IN_PAST_06_12 2.25 score PLING_QUERY 1.0 score SHOPIFY_IMG_NOT_RCVD_SFY 0.75 score T_FILL_THIS_FORM_SHORT 0.25 score T_REMOTE_IMAGE 0.25 score STOX_REPLY_TYPE 2.0 score STOX_REPLY_TYPE_WITHOUT_QUOTES 3.0 score SUSPICIOUS_RECIPS 2.5 # ============================ # Spam Eating Monkey DNSBL lists # ============================ header RCVD_IN_SEM_BACKSCATTER eval:check_rbl('sembackscatter-lastexternal', 'backscatter.spameatingmonkey.net') describe RCVD_IN_SEM_BACKSCATTER Received from an IP listed by Spam Eating Monkey Backscatter list tflags RCVD_IN_SEM_BACKSCATTER net score RCVD_IN_SEM_BACKSCATTER 3.0 header RCVD_IN_SEM_BLACK eval:check_rbl('semblack-lastexternal', 'bl.spameatingmonkey.net') tflags RCVD_IN_SEM_BLACK net describe RCVD_IN_SEM_BLACK Received from an IP listed by Spam Eating Monkey Blocklist score RCVD_IN_SEM_BLACK 3.0 header RCVD_IN_SEM_NETBLACK eval:check_rbl('semnetblack-lastexternal', 'netbl.spameatingmonkey.net') tflags RCVD_IN_SEM_NETBLACK net describe RCVD_IN_SEM_NETBLACK Received from an IP listed by Spam Eating Monkeys Network Blocklist score RCVD_IN_SEM_NETBLACK 1.5 urirhssub SEM_FRESH30 fresh30.spameatingmonkey.net. A 2 body SEM_FRESH30 eval:check_uridnsbl('SEM_FRESH30') describe SEM_FRESH30 Contains a domain registered less than 30 days ago tflags SEM_FRESH30 net score SEM_FRESH30 3.0 urirhssub SEM_URI_BLACK uribl.spameatingmonkey.net. A 2 body SEM_URI_BLACK eval:check_uridnsbl('SEM_URI') describe SEM_URI_BLACK Contains a URI listed by Spam Eating Monkeys URI Blocklist tflags SEM_URI_BLACK net score SEM_URI_BLACK 3.5 # ============================ # JunkEmailFilter HostKarma DNSBL & DNSWL # ============================ header __RCVD_IN_HOSTKARMA eval:check_rbl('hostkarma', 'hostkarma.junkemailfilter.com.') describe __RCVD_IN_HOSTKARMA Sender listed in JunkEmailFilter tflags __RCVD_IN_HOSTKARMA net header RCVD_IN_HOSTKARMA_W eval:check_rbl_sub('hostkarma','127.0.0.1') describe RCVD_IN_HOSTKARMA_W Sender listed in HOSTKARMA-WHITE tflags RCVD_IN_HOSTKARMA_W net nice score RCVD_IN_HOSTKARMA_W -3.5 header RCVD_IN_HOSTKARMA_BL eval:check_rbl_sub('hostkarma','127.0.0.2') describe RCVD_IN_HOSTKARMA_BL Sender listed in HOSTKARMA-BLACK tflags RCVD_IN_HOSTKARMA_BL net score RCVD_IN_HOSTKARMA_BL 3.0 header RCVD_IN_HOSTKARMA_BR eval:check_rbl_sub('hostkarma','127.0.0.4') describe RCVD_IN_HOSTKARMA_BR Sender listed in HOSTKARMA-BROWN tflags RCVD_IN_HOSTKARMA_BR net score RCVD_IN_HOSTKARMA_BR 1.25 # ============================ # SpamRATS DNSBL # ============================ header __RCVD_IN_SPAMRATS eval:check_rbl('spamrats', 'all.spamrats.com.') describe __RCVD_IN_SPAMRATS SPAMRATS: sender is listed in SpamRATS tflags __RCVD_IN_SPAMRATS net reuse __RCVD_IN_SPAMRATS header RCVD_IN_SPAMRATS_DYNA eval:check_rbl_sub('spamrats','127.0.0.36') describe RCVD_IN_SPAMRATS_DYNA RATS-Dyna: sent directly from dynamic IP address tflags RCVD_IN_SPAMRATS_DYNA net reuse RCVD_IN_SPAMRATS_DYNA score RCVD_IN_SPAMRATS_DYNA 2.25 header RCVD_IN_SPAMRATS_NOPTR eval:check_rbl_sub('spamrats','127.0.0.37') describe RCVD_IN_SPAMRATS_NOPTR RATS-NoPtr: sender has no reverse DNS tflags RCVD_IN_SPAMRATS_NOPTR net reuse RCVD_IN_SPAMRATS_NOPTR score RCVD_IN_SPAMRATS_NOPTR 2.5 header RCVD_IN_SPAMRATS_SPAM eval:check_rbl_sub('spamrats','127.0.0.38') describe RCVD_IN_SPAMRATS_SPAM RATS-Spam: sender is a spam source tflags RCVD_IN_SPAMRATS_SPAM net reuse RCVD_IN_SPAMRATS_SPAM score RCVD_IN_SPAMRATS_SPAM 5.5 # ============================ # UCEPROTECT # ============================ header RCVD_IN_UCEPROTECT_LEVEL_1 eval:check_rbl('uceprotect1', 'dnsbl-1.uceprotect.net.') describe RCVD_IN_UCEPROTECT_LEVEL_1 Sender IP listed in UCEPROTECT Level 1 tflags RCVD_IN_UCEPROTECT_LEVEL_1 net score RCVD_IN_UCEPROTECT_LEVEL_1 4.0 header RCVD_IN_UCEPROTECT_LEVEL_2 eval:check_rbl('uceprotect2', 'dnsbl-2.uceprotect.net.') describe RCVD_IN_UCEPROTECT_LEVEL_2 Sender IP listed in UCEPROTECT Level 2 tflags RCVD_IN_UCEPROTECT_LEVEL_2 net score RCVD_IN_UCEPROTECT_LEVEL_2 1.25 # ============================ # Abusix Guardian Mail Relay # ============================ header __RCVD_IN_ABUSIX eval:check_rbl('abusix', '<API_KEY>.combined.mail.abusix.zone.') describe __RCVD_IN_ABUSIX Received via a relay in Abusix Guardian Mail tflags __RCVD_IN_ABUSIX net header RCVD_IN_ABUSIX_BLACK eval:check_rbl_sub('abusix', '^127\.0\.0\.(?:[23]|200)$') describe RCVD_IN_ABUSIX_BLACK Received via a relay in Abusix Guardian Mail Black tflags RCVD_IN_ABUSIX_BLACK net score RCVD_IN_ABUSIX_BLACK 5.5 header RCVD_IN_ABUSIX_EXPLOIT eval:check_rbl_sub('abusix', '127.0.0.4') describe RCVD_IN_ABUSIX_EXPLOIT Received via a relay in Abusix Guardian Mail Exploit tflags RCVD_IN_ABUSIX_EXPLOIT net score RCVD_IN_ABUSIX_EXPLOIT 6.0 header RCVD_IN_ABUSIX_DYN eval:check_rbl('abusix_dyn', '<API_KEY>.combined.mail.abusix.zone.', '^127\.0\.0\.1[12]$') describe RCVD_IN_ABUSIX_DYN Received via a relay in Abusix Guardian Mail Dynamic tflags RCVD_IN_ABUSIX_DYN net score RCVD_IN_ABUSIX_DYN 1.5 header RCVD_IN_ABUSIX_WHITE eval:check_rbl('abusix_white', '<API_KEY>.combined.mail.abusix.zone.', '127.0.2.1') describe RCVD_IN_ABUSIX_WHITE Received via a relay in Abusix Guardian Mail White tflags RCVD_IN_ABUSIX_WHITE nice net score RCVD_IN_ABUSIX_WHITE -1.5 urirhsbl URIBL_ABUSIX_DBLACK <API_KEY>.dblack.mail.abusix.zone. A body URIBL_ABUSIX_DBLACK eval:check_uridnsbl('URIBL_ABUSIX_DBLACK') describe URIBL_ABUSIX_DBLACK Contains a spam URL listed in the Abusix domain blocklist tflags URIBL_ABUSIX_DBLACK net score URIBL_ABUSIX_DBLACK 6.0 urirhssub URIBL_ABUSIX_WHITE <API_KEY>.white.mail.abusix.zone. A 127.0.2.1 body URIBL_ABUSIX_WHITE eval:check_uridnsbl('URIBL_ABUSIX_WHITE') describe URIBL_ABUSIX_WHITE Contains a domain listed in the Abusix domain whitelist tflags URIBL_ABUSIX_WHITE nice net score URIBL_ABUSIX_WHITE -0.25 # ============================ # Ascams RBLs (IP Reputation) # ============================ header RCVD_IN_ASCAMS_BLOCK eval:check_rbl('ascams_block', 'block.ascams.com.') describe RCVD_IN_ASCAMS_BLOCK Sender listed in Ascams Block RBL tflags RCVD_IN_ASCAMS_BLOCK net score RCVD_IN_ASCAMS_BLOCK 1.25 header RCVD_IN_ASCAMS_DROP eval:check_rbl('ascams_white', 'dnsbl.ascams.com.') describe RCVD_IN_ASCAMS_DROP Sender listed in Ascams DROP list tflags RCVD_IN_ASCAMS_DROP nice net score RCVD_IN_ASCAMS_DROP 3.0 # ============================ # DroneBL DNSBL # ============================ header RCVD_IN_DRONEBL eval:check_rbl('dronebl', 'dnsbl.dronebl.org.') describe RCVD_IN_DRONEBL Sender listed in DroneBL (suspected bot/malware) tflags RCVD_IN_DRONEBL net score RCVD_IN_DRONEBL 3.0 # ============================ # GBUDB Truncate DNSBL # ============================ header RCVD_IN_GBUDB_TRUNCATE eval:check_rbl('gbudb', 'truncate.gbudb.net.') describe RCVD_IN_GBUDB_TRUNCATE Sender listed in GBUDB Truncate tflags RCVD_IN_GBUDB_TRUNCATE net score RCVD_IN_GBUDB_TRUNCATE 4.0 # ============================ # Usenix S5H # ============================ header RCVD_IN_S5H_BL eval:check_rbl_txt('s5hbl', 'all.s5h.net.') describe RCVD_IN_S5H_BL Listed at all.s5h.net tflags RCVD_IN_S5H_BL net score RCVD_IN_S5H_BL 0.5 # ============================ # Backscatterer.org # ============================ header RCVD_IN_BACKSCATTERER eval:check_rbl('backscatterer', 'ips.backscatterer.org.') describe RCVD_IN_BACKSCATTERER IP listed in Backscatterer (backscatter spam) tflags RCVD_IN_BACKSCATTERER net score RCVD_IN_BACKSCATTERER 3.5 -
@d19dotca to the rescue once again 🦸 Thanks Dustin! I signed up for an Abusix account. Once signed up, I had to go to the subscription page and activate the "start with free plan" as they also have a free trial for their pro plan. API key is already created and easily accessible from the dashboard. Perfect!
-
Okay everyone... I've spent the past month really fine-tuning the SpamAssassin rules (especially after SpamAssassin was upgraded to 4.0 with Cloudron 8.3), and it seems to be working quite well for me. Spam filtering is never perfect, but it has improved a lot since the last time I took a look at the rules. The list is much longer now, and I added many more rules along with some additional lists for extra checks too.
If you want to use Abusix (which I've found to be very reliable), then you'll need a free API key, and can replace <API_KEY> in the list below with your own.
As always, your own mileage may vary, but this should be an effective SpamAssassin rule set to use. Good luck.

# ============================ # Allowlist / Blocklist Rules # ============================ score USER_IN_BLOCKLIST 50.0 score USER_IN_ALL_SPAM_TO -50.0 score USER_IN_MORE_SPAM_TO -10.0 score USER_IN_WELCOMELIST -50.0 ## Block specific recipients/senders blocklist_from <EMAIL> ## Allowlist specific recipients/senders welcomelist_from <EMAIL> # ============================ # Bayesian Filtering (BAYES) # ============================ bayes_auto_learn 1 bayes_auto_learn_threshold_nonspam -4.0 bayes_auto_learn_threshold_spam 12.0 score BAYES_00 -6.0 score BAYES_05 -4.0 score BAYES_20 1.5 score BAYES_40 2.5 score BAYES_50 3.25 score BAYES_60 3.75 score BAYES_80 4.25 score BAYES_95 5.5 score BAYES_99 7.0 score BAYES_999 7.5 # ============================ # DNS-based Blocklists (DNSBL) # ============================ ## DNS Blocklists score RCVD_IN_BL_SPAMCOP_NET 2.5 score RCVD_IN_MSPIKE_BL 0.0 score RCVD_IN_MSPIKE_L2 1.0 score RCVD_IN_MSPIKE_L3 1.5 score RCVD_IN_MSPIKE_L4 3.5 score RCVD_IN_MSPIKE_L5 5.0 score RCVD_IN_MSPIKE_ZBI 4.0 score RCVD_IN_PBL 3.5 score RCVD_IN_SBL 5.0 score RCVD_IN_SBL_CSS 4.0 score RCVD_IN_VALIDITY_RPBL 1.5 score RCVD_IN_XBL 6.0 score RCVD_IN_ZEN_BLOCKED 0.0 score RCVD_IN_ZEN_BLOCKED_OPENDNS 0.0 ## DNS Whitelists score RCVD_IN_DNSWL_BLOCKED 0.0 score RCVD_IN_DNSWL_HI -6.0 score RCVD_IN_DNSWL_LOW -2.5 score RCVD_IN_DNSWL_MED -4.5 score RCVD_IN_DNSWL_NONE 0.0 score RCVD_IN_MSPIKE_H2 -1.0 score RCVD_IN_MSPIKE_H3 -1.5 score RCVD_IN_MSPIKE_H4 -3.5 score RCVD_IN_MSPIKE_H5 -5.0 score RCVD_IN_MSPIKE_WL 0.0 # ============================ # URI Blocklists (URIBL) # ============================ score URIBL_ABUSE_SURBL 6.0 score URIBL_BLACK 7.0 score URIBL_CR_SURBL 3.5 score URIBL_CSS 3.0 score URIBL_CSS_A 3.0 score URIBL_DBL_ABUSE_BOTCC 5.5 score URIBL_DBL_ABUSE_MALW 5.5 score URIBL_DBL_ABUSE_PHISH 5.5 score URIBL_DBL_ABUSE_REDIR 2.0 score URIBL_DBL_ABUSE_SPAM 5.5 score URIBL_DBL_BLOCKED 0.0 score URIBL_DBL_BLOCKED_OPENDNS 0.0 score URIBL_DBL_BOTNETCC 5.5 score URIBL_DBL_ERROR 0.0 score URIBL_DBL_MALWARE 5.5 score URIBL_DBL_PHISH 5.5 score URIBL_DBL_SPAM 5.5 score URIBL_GREY 0.5 score URIBL_MW_SURBL 5.0 score URIBL_PH_SURBL 5.0 score URIBL_RED 2.0 score URIBL_RHS_DOB 2.0 score URIBL_SBL 4.0 score URIBL_SBL_A 3.0 score URIBL_ZEN_BLOCKED 0.0 score URIBL_ZEN_BLOCKED_OPENDNS 0.0 # ============================ # Email Authentication (SPF/DKIM/ARC) # ============================ ## DKIM score DKIM_INVALID 2.0 score DKIM_ADSP_ALL 2.0 score DKIM_ADSP_CUSTOM_MED 1.5 score DKIM_ADSP_NXDOMAIN 4.5 score DKIM_SIGNED 0.0 score DKIM_VALID 0.0 score DKIM_VALID_AU 0.0 score DKIM_VALID_EF 0.0 score DKIM_VERIFIED 0.0 score DKIMWL_BL 3.0 score DKIMWL_WL_HIGH -6.0 score DKIMWL_WL_MED -4.0 score DKIMWL_WL_MEDHI -4.5 score USER_IN_DEF_DKIM_WL -6.0 ## SPF score FORGED_SPF_HELO 4.0 score SPF_FAIL 4.0 score SPF_HELO_FAIL 2.5 score SPF_HELO_NEUTRAL 1.0 score SPF_HELO_NONE 0.25 score SPF_HELO_PASS -1.0 score SPF_HELO_SOFTFAIL 4.0 score SPF_NEUTRAL 0.0 score SPF_NONE 1.0 score SPF_PASS -1.0 score SPF_SOFTFAIL 1.5 score T_SPF_PERMERROR 2.0 score T_SPF_TEMPERROR 0.0 score USER_IN_DEF_SPF_WL -6.0 ## ARC score ARC_INVALID 2.0 score ARC_SIGNED 0.0 score ARC_VALID -0.5 # ============================ # HTML & MIME Structure Rules # ============================ score HTML_FONT_LOW_CONTRAST 0.0 score HTML_FONT_SIZE_LARGE 2.0 score HTML_FONT_TINY_NORDNS 0.0 score HTML_IMAGE_ONLY_04 1.25 score HTML_IMAGE_ONLY_08 1.25 score HTML_IMAGE_ONLY_12 1.25 score HTML_IMAGE_ONLY_16 1.25 score HTML_IMAGE_ONLY_20 1.25 score HTML_IMAGE_ONLY_24 1.25 score HTML_IMAGE_ONLY_28 1.25 score HTML_IMAGE_ONLY_32 1.25 score HTML_MESSAGE 0.0 score HTML_MIME_NO_HTML_TAG 0.5 score HTML_OBFUSCATE_05_10 0.5 score HTML_OBFUSCATE_10_20 1.0 score HTML_OBFUSCATE_20_30 2.0 score HTML_OBFUSCATE_30_40 2.5 score HTML_OBFUSCATE_50_60 3.0 score HTML_OBFUSCATE_70_80 3.5 score HTML_OBFUSCATE_90_100 4.0 score HTML_SHORT_LINK_IMG_1 2.0 score HTML_SHORT_LINK_IMG_2 3.0 score HTML_SHORT_LINK_IMG_3 3.0 score MIME_HTML_MOSTLY 0.0 score MIME_HTML_ONLY 0.0 score MPART_ALT_DIFF 0.5 score MPART_ALT_DIFF_COUNT 0.5 # ============================ # Header / Envelope Heuristics # ============================ score HEADER_FROM_DIFFERENT_DOMAINS 2.0 score MISSING_DATE 2.5 score MISSING_FROM 2.0 score MISSING_HEADERS 2.5 score MISSING_MID 1.0 score MISSING_SUBJECT 1.0 score MSGID_OUTLOOK_INVALID 4.0 score MISSING_HB_SEP 2.0 score TO_NO_BRKTS_FROM_MSSP 1.5 score REPLYTO_WITHOUT_TO_CC 2.5 # ============================ # Freemail & Identity Rules # ============================ score FREEMAIL_ENVFROM_END_DIGIT 1.0 score FREEMAIL_FORGED_REPLYTO 2.25 score FREEMAIL_FROM 0.0 score FREEMAIL_REPLY 0.5 score FREEMAIL_REPLYTO 2.0 score FREEMAIL_REPLYTO_END_DIGIT 0.0 score FROM_LOCAL_DIGITS 1.75 score FROM_EXCESS_BASE64 2.5 score FROM_FMBLA_NEWDOM 2.5 score FROM_FMBLA_NEWDOM14 3.0 score FROM_FMBLA_NEWDOM28 2.5 score FROM_SUSPICIOUS_NTLD 2.0 score FORGED_GMAIL_RCVD 3.0 score FORGED_MUA_OUTLOOK 3.0 score FORGED_YAHOO_RCVD 3.0 # ============================ # Scam, Phishing & Social Engineering # ============================ score ADVANCE_FEE_2 3.0 score ADVANCE_FEE_2_NEW_MONEY 3.0 score ADVANCE_FEE_2_NEW_FORM 3.0 score ADVANCE_FEE_3 3.0 score ADVANCE_FEE_3_NEW 3.0 score ADVANCE_FEE_3_NEW_MONEY 3.0 score ADVANCE_FEE_3_NEW_FORM 3.0 score ADVANCE_FEE_4_NEW 3.0 score ADVANCE_FEE_5_NEW 3.0 score ADVANCE_FEE_5_NEW_FRM_MNY 3.0 score ADVANCE_FEE_5_NEW_MONEY 3.0 score BILLION_DOLLARS 1.0 score DEAR_FRIEND 1.5 score LOTS_OF_MONEY 0.0 score UNCLAIMED_MONEY 4.0 score URG_BIZ 1.5 score FUZZY_CLICK_HERE 1.5 score FUZZY_CREDIT 2.0 score FUZZY_IMPORTANT 2.0 score FUZZY_SECURITY 2.25 score FUZZY_UNSUBSCRIBE 1.0 score SUBJ_AS_SEEN 0.75 score SUBJ_DOLLARS 0.25 score SUBJ_YOUR_DEBT 2.5 score SUBJ_YOUR_FAMILY 0.75 # ============================ # Transport / Network Reputation Rules # ============================ score NO_RDNS_DOTCOM_HELO 3.0 score RDNS_DYNAMIC 3.5 score RDNS_LOCALHOST 3.5 score RDNS_NONE 2.25 score RCVD_HELO_IP_MISMATCH 1.75 score RCVD_ILLEGAL_IP 4.0 score PDS_BAD_THREAD_QP_64 1.5 score TBIRD_SUSP_MIME_BDRY 2.5 score SPAMMY_XMAILER 2.75 score KHOP_HELO_FCRDNS -0.5 score HELO_DYNAMIC_IPADDR 2.0 score HELO_DYNAMIC_SPLIT_IP 2.0 score UNPARSEABLE_RELAY 0.0 # ============================ # URI & Link Obfuscation # ============================ score URI_HEX 2.5 score URI_NO_WWW_BIZ_CGI 2.5 score URI_NO_WWW_INFO_CGI 2.5 score URI_OBFU_WWW 3.0 score URI_TRUNCATED 2.5 score HTTPS_HTTP_MISMATCH 0.25 score WEIRD_PORT 4.5 # ============================ # Miscellaneous Heuristics & Content Triggers # ============================ score ENV_AND_HDR_SPF_MATCH -4.0 score DATE_IN_FUTURE_06_12 2.25 score DATE_IN_PAST_03_06 2.25 score DATE_IN_PAST_06_12 2.25 score PLING_QUERY 1.0 score SHOPIFY_IMG_NOT_RCVD_SFY 0.75 score T_FILL_THIS_FORM_SHORT 0.25 score T_REMOTE_IMAGE 0.25 score STOX_REPLY_TYPE 2.0 score STOX_REPLY_TYPE_WITHOUT_QUOTES 3.0 score SUSPICIOUS_RECIPS 2.5 # ============================ # Spam Eating Monkey DNSBL lists # ============================ header RCVD_IN_SEM_BACKSCATTER eval:check_rbl('sembackscatter-lastexternal', 'backscatter.spameatingmonkey.net') describe RCVD_IN_SEM_BACKSCATTER Received from an IP listed by Spam Eating Monkey Backscatter list tflags RCVD_IN_SEM_BACKSCATTER net score RCVD_IN_SEM_BACKSCATTER 3.0 header RCVD_IN_SEM_BLACK eval:check_rbl('semblack-lastexternal', 'bl.spameatingmonkey.net') tflags RCVD_IN_SEM_BLACK net describe RCVD_IN_SEM_BLACK Received from an IP listed by Spam Eating Monkey Blocklist score RCVD_IN_SEM_BLACK 3.0 header RCVD_IN_SEM_NETBLACK eval:check_rbl('semnetblack-lastexternal', 'netbl.spameatingmonkey.net') tflags RCVD_IN_SEM_NETBLACK net describe RCVD_IN_SEM_NETBLACK Received from an IP listed by Spam Eating Monkeys Network Blocklist score RCVD_IN_SEM_NETBLACK 1.5 urirhssub SEM_FRESH30 fresh30.spameatingmonkey.net. A 2 body SEM_FRESH30 eval:check_uridnsbl('SEM_FRESH30') describe SEM_FRESH30 Contains a domain registered less than 30 days ago tflags SEM_FRESH30 net score SEM_FRESH30 3.0 urirhssub SEM_URI_BLACK uribl.spameatingmonkey.net. A 2 body SEM_URI_BLACK eval:check_uridnsbl('SEM_URI') describe SEM_URI_BLACK Contains a URI listed by Spam Eating Monkeys URI Blocklist tflags SEM_URI_BLACK net score SEM_URI_BLACK 3.5 # ============================ # JunkEmailFilter HostKarma DNSBL & DNSWL # ============================ header __RCVD_IN_HOSTKARMA eval:check_rbl('hostkarma', 'hostkarma.junkemailfilter.com.') describe __RCVD_IN_HOSTKARMA Sender listed in JunkEmailFilter tflags __RCVD_IN_HOSTKARMA net header RCVD_IN_HOSTKARMA_W eval:check_rbl_sub('hostkarma','127.0.0.1') describe RCVD_IN_HOSTKARMA_W Sender listed in HOSTKARMA-WHITE tflags RCVD_IN_HOSTKARMA_W net nice score RCVD_IN_HOSTKARMA_W -3.5 header RCVD_IN_HOSTKARMA_BL eval:check_rbl_sub('hostkarma','127.0.0.2') describe RCVD_IN_HOSTKARMA_BL Sender listed in HOSTKARMA-BLACK tflags RCVD_IN_HOSTKARMA_BL net score RCVD_IN_HOSTKARMA_BL 3.0 header RCVD_IN_HOSTKARMA_BR eval:check_rbl_sub('hostkarma','127.0.0.4') describe RCVD_IN_HOSTKARMA_BR Sender listed in HOSTKARMA-BROWN tflags RCVD_IN_HOSTKARMA_BR net score RCVD_IN_HOSTKARMA_BR 1.25 # ============================ # SpamRATS DNSBL # ============================ header __RCVD_IN_SPAMRATS eval:check_rbl('spamrats', 'all.spamrats.com.') describe __RCVD_IN_SPAMRATS SPAMRATS: sender is listed in SpamRATS tflags __RCVD_IN_SPAMRATS net reuse __RCVD_IN_SPAMRATS header RCVD_IN_SPAMRATS_DYNA eval:check_rbl_sub('spamrats','127.0.0.36') describe RCVD_IN_SPAMRATS_DYNA RATS-Dyna: sent directly from dynamic IP address tflags RCVD_IN_SPAMRATS_DYNA net reuse RCVD_IN_SPAMRATS_DYNA score RCVD_IN_SPAMRATS_DYNA 2.25 header RCVD_IN_SPAMRATS_NOPTR eval:check_rbl_sub('spamrats','127.0.0.37') describe RCVD_IN_SPAMRATS_NOPTR RATS-NoPtr: sender has no reverse DNS tflags RCVD_IN_SPAMRATS_NOPTR net reuse RCVD_IN_SPAMRATS_NOPTR score RCVD_IN_SPAMRATS_NOPTR 2.5 header RCVD_IN_SPAMRATS_SPAM eval:check_rbl_sub('spamrats','127.0.0.38') describe RCVD_IN_SPAMRATS_SPAM RATS-Spam: sender is a spam source tflags RCVD_IN_SPAMRATS_SPAM net reuse RCVD_IN_SPAMRATS_SPAM score RCVD_IN_SPAMRATS_SPAM 5.5 # ============================ # UCEPROTECT # ============================ header RCVD_IN_UCEPROTECT_LEVEL_1 eval:check_rbl('uceprotect1', 'dnsbl-1.uceprotect.net.') describe RCVD_IN_UCEPROTECT_LEVEL_1 Sender IP listed in UCEPROTECT Level 1 tflags RCVD_IN_UCEPROTECT_LEVEL_1 net score RCVD_IN_UCEPROTECT_LEVEL_1 4.0 header RCVD_IN_UCEPROTECT_LEVEL_2 eval:check_rbl('uceprotect2', 'dnsbl-2.uceprotect.net.') describe RCVD_IN_UCEPROTECT_LEVEL_2 Sender IP listed in UCEPROTECT Level 2 tflags RCVD_IN_UCEPROTECT_LEVEL_2 net score RCVD_IN_UCEPROTECT_LEVEL_2 1.25 # ============================ # Abusix Guardian Mail Relay # ============================ header __RCVD_IN_ABUSIX eval:check_rbl('abusix', '<API_KEY>.combined.mail.abusix.zone.') describe __RCVD_IN_ABUSIX Received via a relay in Abusix Guardian Mail tflags __RCVD_IN_ABUSIX net header RCVD_IN_ABUSIX_BLACK eval:check_rbl_sub('abusix', '^127\.0\.0\.(?:[23]|200)$') describe RCVD_IN_ABUSIX_BLACK Received via a relay in Abusix Guardian Mail Black tflags RCVD_IN_ABUSIX_BLACK net score RCVD_IN_ABUSIX_BLACK 5.5 header RCVD_IN_ABUSIX_EXPLOIT eval:check_rbl_sub('abusix', '127.0.0.4') describe RCVD_IN_ABUSIX_EXPLOIT Received via a relay in Abusix Guardian Mail Exploit tflags RCVD_IN_ABUSIX_EXPLOIT net score RCVD_IN_ABUSIX_EXPLOIT 6.0 header RCVD_IN_ABUSIX_DYN eval:check_rbl('abusix_dyn', '<API_KEY>.combined.mail.abusix.zone.', '^127\.0\.0\.1[12]$') describe RCVD_IN_ABUSIX_DYN Received via a relay in Abusix Guardian Mail Dynamic tflags RCVD_IN_ABUSIX_DYN net score RCVD_IN_ABUSIX_DYN 1.5 header RCVD_IN_ABUSIX_WHITE eval:check_rbl('abusix_white', '<API_KEY>.combined.mail.abusix.zone.', '127.0.2.1') describe RCVD_IN_ABUSIX_WHITE Received via a relay in Abusix Guardian Mail White tflags RCVD_IN_ABUSIX_WHITE nice net score RCVD_IN_ABUSIX_WHITE -1.5 urirhsbl URIBL_ABUSIX_DBLACK <API_KEY>.dblack.mail.abusix.zone. A body URIBL_ABUSIX_DBLACK eval:check_uridnsbl('URIBL_ABUSIX_DBLACK') describe URIBL_ABUSIX_DBLACK Contains a spam URL listed in the Abusix domain blocklist tflags URIBL_ABUSIX_DBLACK net score URIBL_ABUSIX_DBLACK 6.0 urirhssub URIBL_ABUSIX_WHITE <API_KEY>.white.mail.abusix.zone. A 127.0.2.1 body URIBL_ABUSIX_WHITE eval:check_uridnsbl('URIBL_ABUSIX_WHITE') describe URIBL_ABUSIX_WHITE Contains a domain listed in the Abusix domain whitelist tflags URIBL_ABUSIX_WHITE nice net score URIBL_ABUSIX_WHITE -0.25 # ============================ # Ascams RBLs (IP Reputation) # ============================ header RCVD_IN_ASCAMS_BLOCK eval:check_rbl('ascams_block', 'block.ascams.com.') describe RCVD_IN_ASCAMS_BLOCK Sender listed in Ascams Block RBL tflags RCVD_IN_ASCAMS_BLOCK net score RCVD_IN_ASCAMS_BLOCK 1.25 header RCVD_IN_ASCAMS_DROP eval:check_rbl('ascams_white', 'dnsbl.ascams.com.') describe RCVD_IN_ASCAMS_DROP Sender listed in Ascams DROP list tflags RCVD_IN_ASCAMS_DROP nice net score RCVD_IN_ASCAMS_DROP 3.0 # ============================ # DroneBL DNSBL # ============================ header RCVD_IN_DRONEBL eval:check_rbl('dronebl', 'dnsbl.dronebl.org.') describe RCVD_IN_DRONEBL Sender listed in DroneBL (suspected bot/malware) tflags RCVD_IN_DRONEBL net score RCVD_IN_DRONEBL 3.0 # ============================ # GBUDB Truncate DNSBL # ============================ header RCVD_IN_GBUDB_TRUNCATE eval:check_rbl('gbudb', 'truncate.gbudb.net.') describe RCVD_IN_GBUDB_TRUNCATE Sender listed in GBUDB Truncate tflags RCVD_IN_GBUDB_TRUNCATE net score RCVD_IN_GBUDB_TRUNCATE 4.0 # ============================ # Usenix S5H # ============================ header RCVD_IN_S5H_BL eval:check_rbl_txt('s5hbl', 'all.s5h.net.') describe RCVD_IN_S5H_BL Listed at all.s5h.net tflags RCVD_IN_S5H_BL net score RCVD_IN_S5H_BL 0.5 # ============================ # Backscatterer.org # ============================ header RCVD_IN_BACKSCATTERER eval:check_rbl('backscatterer', 'ips.backscatterer.org.') describe RCVD_IN_BACKSCATTERER IP listed in Backscatterer (backscatter spam) tflags RCVD_IN_BACKSCATTERER net score RCVD_IN_BACKSCATTERER 3.5 -
@murgero said in Sharing custom SpamAssassin Rules:
@d19dotca does this just go into email -> Spam Filter -> Custom Spam Assassin Settings?
Yes, it goes right there. Basically from the Mail page > Spam filtering > Custom Spamassassin Rules box.
You can copy & paste the entire thing, but do note a few items just in case:
- You will need to likely remove the
blocklist_fromorwelcomelist_fromlines unless you have emails to place in those two sections already, I left those there just for an example. - If you want to use the DNSBLs from Abusix then you'll need to use your own API key (it's free for under 5,000 queries per day averaged over 7 days, it seems to work great and I highly recommend it).
The rest though you can basically copy & paste directly. Of course YMMV as they say, but this list works pretty well for me, or at least is a noticeable improvement over the rule tweaks I was using last year.
- You will need to likely remove the
-
@d19dotca awesome stuff!
Just setup with my own api key of Abusix and I will happly report back after some time.
Where is your tipping jar? Did not find it on your webpage www.d19.ca
Did not find it on your webpage www.d19.ca -
Aww thank you for the compliment!
 Honestly I’ve never started a tip jar but that’s probably a good idea for me to start one.
Honestly I’ve never started a tip jar but that’s probably a good idea for me to start one. -
@d19dotca Many thanks for sharing this. I'd like to suggest another addition based on one nasty abuse I've seen: unsubscribe links that use http instead of https, hoping that browser security blocks/warnings will cause users not to follow through and unsubscribe. Anyone not using https for anything these days is not worthy of my time:) This puts them where they belong:
# Rule to detect unsubscribe links that do not use HTTPS body UNSUB_LINK_HTTP /unsubscribe.*http:\/\//i describe UNSUB_LINK_HTTP Unsubscribe link does not use HTTPS score UNSUB_LINK_HTTP 10.0 -
@d19dotca Many thanks for sharing this. I'd like to suggest another addition based on one nasty abuse I've seen: unsubscribe links that use http instead of https, hoping that browser security blocks/warnings will cause users not to follow through and unsubscribe. Anyone not using https for anything these days is not worthy of my time:) This puts them where they belong:
# Rule to detect unsubscribe links that do not use HTTPS body UNSUB_LINK_HTTP /unsubscribe.*http:\/\//i describe UNSUB_LINK_HTTP Unsubscribe link does not use HTTPS score UNSUB_LINK_HTTP 10.0@crazybrad Excellent pattern!
-
@d19dotca Many thanks for sharing this. I'd like to suggest another addition based on one nasty abuse I've seen: unsubscribe links that use http instead of https, hoping that browser security blocks/warnings will cause users not to follow through and unsubscribe. Anyone not using https for anything these days is not worthy of my time:) This puts them where they belong:
# Rule to detect unsubscribe links that do not use HTTPS body UNSUB_LINK_HTTP /unsubscribe.*http:\/\//i describe UNSUB_LINK_HTTP Unsubscribe link does not use HTTPS score UNSUB_LINK_HTTP 10.0@crazybrad said in Sharing custom SpamAssassin Rules:
@d19dotca Many thanks for sharing this. I'd like to suggest another addition based on one nasty abuse I've seen: unsubscribe links that use http instead of https, hoping that browser security blocks/warnings will cause users not to follow through and unsubscribe. Anyone not using https for anything these days is not worthy of my time:) This puts them where they belong:
# Rule to detect unsubscribe links that do not use HTTPS body UNSUB_LINK_HTTP /unsubscribe.*http:\/\//i describe UNSUB_LINK_HTTP Unsubscribe link does not use HTTPS score UNSUB_LINK_HTTP 10.0Oh I like that! That’s a great idea!

-
I'm getting a ton of spam from @gmail addresses. It's not possible to address those via rules without affecting all incoming gmail delivery, right?
Also, what DNSBL zones other than Zen.Spamhaus is everyone using?
