Netmaker - manage wireguard networks
-
- https://www.netmaker.io/
- https://github.com/gravitl/netmaker
- https://netmaker.readthedocs.io/en/master/about.html
- https://netmaker.readthedocs.io/en/master/install.html
- https://alternativeto.net/software/netmaker/about/
- https://alternativeto.net/software/netmaker/
- https://forum.cloudron.io/topic/7560/omniedge-decentralised-noconf-mesh-vpn-using-wireguard-alternative-to-zerotier-tailscale-etc
- https://forum.cloudron.io/topic/7563/tailscale-decentralised-noconf-mesh-vpn-using-wireguard-alternative-to-zerotier-etc
- https://forum.cloudron.io/topic/7567/firezone-foss-noconf-mesh-vpn-using-wireguard-alternative-to-zerotier-tailscale-omniedge-netmaker-etc
- https://forum.cloudron.io/topic/7571/netbird-foss-noconf-mesh-vpn-using-wireguard-alternative-to-zerotier-tailscale-omniedge-netmaker-etc
WireGuard
 automation from homelab to enterprise
automation from homelab to enterprise
Create Manage Automate
 ️ WireGuard Networks
️ WireGuard Networks  ️ Admin UI
️ Admin UI  ️ Linux
️ Linux
 ️ Remote Access Gateways
️ Remote Access Gateways  ️ OAuth
️ OAuth  ️ FreeBSD
️ FreeBSD
 ️ Mesh VPNs
️ Mesh VPNs  ️ Private DNS
️ Private DNS  ️ Mac
️ Mac
 ️ Site-to-Site
️ Site-to-Site  ️ Access Control Lists
️ Access Control Lists  ️ Windows
️ Windows(Uses the native Wireguard apps for the clients, so already very mature tried & tested open-source for that part of the overall)

-
Netmaker is source-available, not open-source:-
https://github.com/gravitl/netmaker/blob/master/LICENSE.txtServer Side Public License - Wikipedia
https://en.wikipedia.org/wiki/Server_Side_Public_LicenseJust a heads up!
-
There's an even faster WireguardNT now that avoids all the context switching by running from the kernel.
@robi
WireguardNT is Windows only.On Netmaker, at:-
https://www.reddit.com/r/selfhosted/comments/p2d8a5/netmaker_07_very_fast_linux_server_networking/"Netmaker is a VPN platform built for kernel WireGuard (because of this it can run ~50%+ faster than many similar platforms)."
"...ran some speed tests last week and Netmaker was over 60% faster than Tailscale. This is because we use kernel WireGuard instead of userspace."
-
@robi
WireguardNT is Windows only.On Netmaker, at:-
https://www.reddit.com/r/selfhosted/comments/p2d8a5/netmaker_07_very_fast_linux_server_networking/"Netmaker is a VPN platform built for kernel WireGuard (because of this it can run ~50%+ faster than many similar platforms)."
"...ran some speed tests last week and Netmaker was over 60% faster than Tailscale. This is because we use kernel WireGuard instead of userspace."
-
@robi
I meant Linux kernel Wireguard. -
- https://www.netmaker.io/
- https://github.com/gravitl/netmaker
- https://netmaker.readthedocs.io/en/master/about.html
- https://netmaker.readthedocs.io/en/master/install.html
- https://alternativeto.net/software/netmaker/about/
- https://alternativeto.net/software/netmaker/
- https://forum.cloudron.io/topic/7560/omniedge-decentralised-noconf-mesh-vpn-using-wireguard-alternative-to-zerotier-tailscale-etc
- https://forum.cloudron.io/topic/7563/tailscale-decentralised-noconf-mesh-vpn-using-wireguard-alternative-to-zerotier-etc
- https://forum.cloudron.io/topic/7567/firezone-foss-noconf-mesh-vpn-using-wireguard-alternative-to-zerotier-tailscale-omniedge-netmaker-etc
- https://forum.cloudron.io/topic/7571/netbird-foss-noconf-mesh-vpn-using-wireguard-alternative-to-zerotier-tailscale-omniedge-netmaker-etc
WireGuard
 automation from homelab to enterprise
automation from homelab to enterprise
Create Manage Automate
 ️ WireGuard Networks
️ WireGuard Networks  ️ Admin UI
️ Admin UI  ️ Linux
️ Linux
 ️ Remote Access Gateways
️ Remote Access Gateways  ️ OAuth
️ OAuth  ️ FreeBSD
️ FreeBSD
 ️ Mesh VPNs
️ Mesh VPNs  ️ Private DNS
️ Private DNS  ️ Mac
️ Mac
 ️ Site-to-Site
️ Site-to-Site  ️ Access Control Lists
️ Access Control Lists  ️ Windows
️ Windows(Uses the native Wireguard apps for the clients, so already very mature tried & tested open-source for that part of the overall)


@marcusquinn wow, you’re doing a lot of work on this topic !
They all look interesting but my head is hurting in terms of trying to understand what is best option for me, and what suits packaging for Cloudron best.
Can’t expect you to have an opinion on the first, or even the second of those.
But do you have a view on respective merits of these new candidates ?
(not that we are limited to one of course) -
@marcusquinn wow, you’re doing a lot of work on this topic !
They all look interesting but my head is hurting in terms of trying to understand what is best option for me, and what suits packaging for Cloudron best.
Can’t expect you to have an opinion on the first, or even the second of those.
But do you have a view on respective merits of these new candidates ?
(not that we are limited to one of course)@timconsidine Seems safe enough to try any of the available client apps (Tailscale / OmniEdge both worked easily and instantly for me).
I post them all for the many more eyes and viewpoints to highlight the good, bad and ugly gotchyas of each.
They all seem to be Golang in some way, so that might make packaging easier — but we have to leave it up to the more experienced and enthused to choose to package any or many of them for Cloudron.
My thinking otherwise is that it is best to have one's own Proxmox server, and just make mini-VMs for each of these things using their regular install scripts designed for that.
Personally, I don't think you need self-hosted for the user account management aspect, but it's nice for assurance of being totally off-grid or getting access to more features without subscription costs.
They all look so good though eh! We are certainly spoiled for choice with open-source nowadays, happily open-source publishing seems to becoming a competitive advantage in both cheap network marketing, and assurances needed to attract enterprise clients.
-
@marcusquinn wow, you’re doing a lot of work on this topic !
They all look interesting but my head is hurting in terms of trying to understand what is best option for me, and what suits packaging for Cloudron best.
Can’t expect you to have an opinion on the first, or even the second of those.
But do you have a view on respective merits of these new candidates ?
(not that we are limited to one of course)@timconsidine Note: Netmaker and Fireguard use the native Wireguard app and generate QR codes for connection credentials.
This *might *be a better approach for avoiding lock-in, having a wider community monitoring and updating the client codebase. In which case, that might help you narrow down your options for at-least the priority order in which to go though trying them.
On the flip-side, Tailscale and OmniEdge you can try out immediately, without any need to setup a self-hosted server.
I see no harm in trying them all, we're lucky to have all these optios eh!
-
@timconsidine Note: Netmaker and Fireguard use the native Wireguard app and generate QR codes for connection credentials.
This *might *be a better approach for avoiding lock-in, having a wider community monitoring and updating the client codebase. In which case, that might help you narrow down your options for at-least the priority order in which to go though trying them.
On the flip-side, Tailscale and OmniEdge you can try out immediately, without any need to setup a self-hosted server.
I see no harm in trying them all, we're lucky to have all these optios eh!
-
- https://www.netmaker.io/
- https://github.com/gravitl/netmaker
- https://netmaker.readthedocs.io/en/master/about.html
- https://netmaker.readthedocs.io/en/master/install.html
- https://alternativeto.net/software/netmaker/about/
- https://alternativeto.net/software/netmaker/
- https://forum.cloudron.io/topic/7560/omniedge-decentralised-noconf-mesh-vpn-using-wireguard-alternative-to-zerotier-tailscale-etc
- https://forum.cloudron.io/topic/7563/tailscale-decentralised-noconf-mesh-vpn-using-wireguard-alternative-to-zerotier-etc
- https://forum.cloudron.io/topic/7567/firezone-foss-noconf-mesh-vpn-using-wireguard-alternative-to-zerotier-tailscale-omniedge-netmaker-etc
- https://forum.cloudron.io/topic/7571/netbird-foss-noconf-mesh-vpn-using-wireguard-alternative-to-zerotier-tailscale-omniedge-netmaker-etc
WireGuard
 automation from homelab to enterprise
automation from homelab to enterprise
Create Manage Automate
 ️ WireGuard Networks
️ WireGuard Networks  ️ Admin UI
️ Admin UI  ️ Linux
️ Linux
 ️ Remote Access Gateways
️ Remote Access Gateways  ️ OAuth
️ OAuth  ️ FreeBSD
️ FreeBSD
 ️ Mesh VPNs
️ Mesh VPNs  ️ Private DNS
️ Private DNS  ️ Mac
️ Mac
 ️ Site-to-Site
️ Site-to-Site  ️ Access Control Lists
️ Access Control Lists  ️ Windows
️ Windows(Uses the native Wireguard apps for the clients, so already very mature tried & tested open-source for that part of the overall)


@marcusquinn Mate you're on fire or what?

-
- https://www.netmaker.io/
- https://github.com/gravitl/netmaker
- https://netmaker.readthedocs.io/en/master/about.html
- https://netmaker.readthedocs.io/en/master/install.html
- https://alternativeto.net/software/netmaker/about/
- https://alternativeto.net/software/netmaker/
- https://forum.cloudron.io/topic/7560/omniedge-decentralised-noconf-mesh-vpn-using-wireguard-alternative-to-zerotier-tailscale-etc
- https://forum.cloudron.io/topic/7563/tailscale-decentralised-noconf-mesh-vpn-using-wireguard-alternative-to-zerotier-etc
- https://forum.cloudron.io/topic/7567/firezone-foss-noconf-mesh-vpn-using-wireguard-alternative-to-zerotier-tailscale-omniedge-netmaker-etc
- https://forum.cloudron.io/topic/7571/netbird-foss-noconf-mesh-vpn-using-wireguard-alternative-to-zerotier-tailscale-omniedge-netmaker-etc
WireGuard
 automation from homelab to enterprise
automation from homelab to enterprise
Create Manage Automate
 ️ WireGuard Networks
️ WireGuard Networks  ️ Admin UI
️ Admin UI  ️ Linux
️ Linux
 ️ Remote Access Gateways
️ Remote Access Gateways  ️ OAuth
️ OAuth  ️ FreeBSD
️ FreeBSD
 ️ Mesh VPNs
️ Mesh VPNs  ️ Private DNS
️ Private DNS  ️ Mac
️ Mac
 ️ Site-to-Site
️ Site-to-Site  ️ Access Control Lists
️ Access Control Lists  ️ Windows
️ Windows(Uses the native Wireguard apps for the clients, so already very mature tried & tested open-source for that part of the overall)


@marcusquinn Amazing analysis and great work. I can hat tip NetMaker here as I use it in production for about 20 servers and has revolutionized my administration. I even use a reverse proxy to tunnel back to my Cloudron instance over a NetMaker endpoint.
It's had several breaking changes in the past few months as they get closer to their 1.0, but aside from that, it's been smooth sailing - even behind CGNat (which is a story unto itself).
-
@marcusquinn Mate you're on fire or what?

@micmc Aha, just trying to make a bunch of clients & servers accessible to each other in the simplest possible way across 6 locations.
This whole Mesh VPN area seems to solve that in a very non-technical way, and actually looks like many experienced IT admins have not really explored it, as they already have their comfort zones in the previous ways of doing these things with routers, firewalls and device VPNs etc.
These zero-conf Mesh VPN options are sooooo much easier, faster and less hazardous for time-loss because of one small piece of missing information in what can otherwise be complex setups.
-
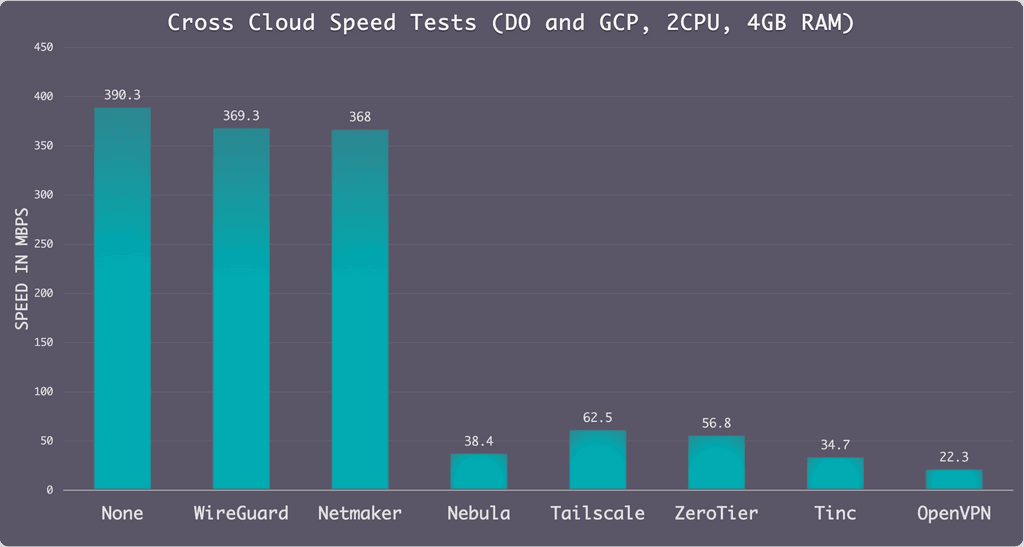
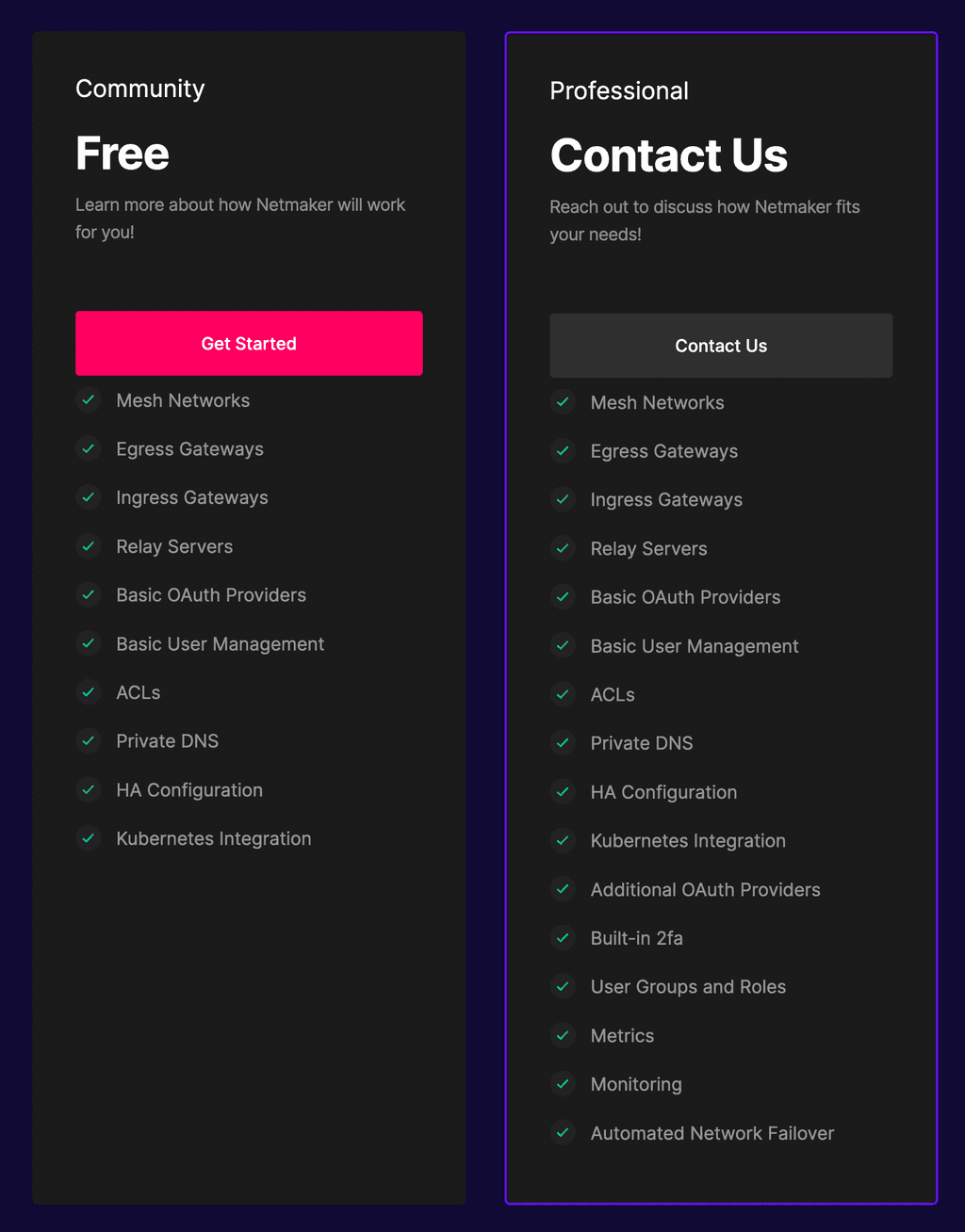
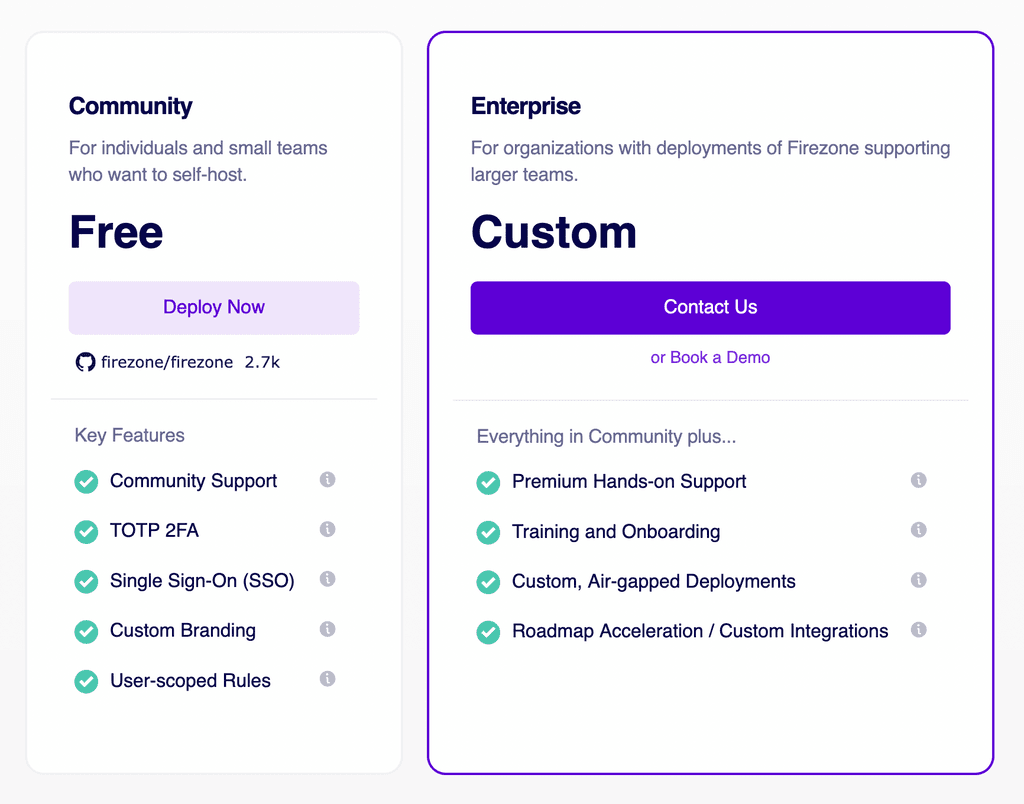
@timconsidine The more I compare each, the more Netmaker seems to be claiming the best speeds, but I guess they would. and it does seem very feature rich - however, Firezone does seem to be suggesting it offers more of the features in it's community edition, that Netmaker suggests are for Enterprise custom:
Netmaker Pricing/Features
Firezone Pricing/Features
If you compare GitHub stars and Twitter followers, then Netmaker is way ahead.
I really do think Cloudron would benefit from having both options though, the best way to compare anything is trying to live with it.
Intro from the founder seems reassuring for his Cisco experience:
Jamil Bou Kheir@jamilbk
Maker
Hi Product Hunt!I'm Jamil, the CEO of Firezone. I'm here with my co-founder and COO @jgong.
While working as a security automation engineer at Cisco I found myself needing to set up remote access for my team into various internal private networks for running security tests and scanning networks. We quickly found OpenVPN cumbersome and complicated to manage, and often found ourselves frustrated by its slow and unreliable connections.
Then we discovered WireGuard
 . WireGuard
. WireGuard is an absolute godsend to anyone needing a layer 3/4 tunnel. It boasts 3-4x faster throughput than OpenVPN, reconnect times measured in milliseconds, and typically incurs no noticeable latency overhead vs a direct connection.
is an absolute godsend to anyone needing a layer 3/4 tunnel. It boasts 3-4x faster throughput than OpenVPN, reconnect times measured in milliseconds, and typically incurs no noticeable latency overhead vs a direct connection.WireGuard
 is a great foundation -- but it's lacking critical features like 2FA, SSO, and more that prevent it from being used effectively in team environments.
is a great foundation -- but it's lacking critical features like 2FA, SSO, and more that prevent it from being used effectively in team environments.So we built Firezone.
Firezone's an intuitive, snappy web UI bundled as a Linux package designed to make it as painlesss as possible to manage secure remote access for your team.
Use Firezone to manage secure remote access to applications in your private cloud, funnel traffic through a single egress gateway for your team, establish a reverse tunnel to a host behind NAT, or simply ensure that the first hop from your teams' laptops is encrypted when connecting from untrusted cafe and airport WiFi.
What makes Firezone different?
We're 100% open source and plan to remain that way. We're also self-hosted; we believe virtual private networks should remain private. Firezone can be deployed in air-gapped environments such that none of your traffic ever touches our servers.
What's next?
Firezone is still in its infancy; we've got tons of new features in the pipeline for release later this year. Now's a great time to check it out and offer your feedback to steer development! We just launched our public Beta program and will be giving early adopters license keys to paid Firezone tiers when they become available. Register to receive yours! https://e04kusl9oz5.typeform.com...
-
@timconsidine The more I compare each, the more Netmaker seems to be claiming the best speeds, but I guess they would. and it does seem very feature rich - however, Firezone does seem to be suggesting it offers more of the features in it's community edition, that Netmaker suggests are for Enterprise custom:
Netmaker Pricing/Features

Firezone Pricing/Features

If you compare GitHub stars and Twitter followers, then Netmaker is way ahead.
I really do think Cloudron would benefit from having both options though, the best way to compare anything is trying to live with it.
Intro from the founder seems reassuring for his Cisco experience:
Jamil Bou Kheir@jamilbk
Maker
Hi Product Hunt!I'm Jamil, the CEO of Firezone. I'm here with my co-founder and COO @jgong.
While working as a security automation engineer at Cisco I found myself needing to set up remote access for my team into various internal private networks for running security tests and scanning networks. We quickly found OpenVPN cumbersome and complicated to manage, and often found ourselves frustrated by its slow and unreliable connections.
Then we discovered WireGuard
 . WireGuard
. WireGuard is an absolute godsend to anyone needing a layer 3/4 tunnel. It boasts 3-4x faster throughput than OpenVPN, reconnect times measured in milliseconds, and typically incurs no noticeable latency overhead vs a direct connection.
is an absolute godsend to anyone needing a layer 3/4 tunnel. It boasts 3-4x faster throughput than OpenVPN, reconnect times measured in milliseconds, and typically incurs no noticeable latency overhead vs a direct connection.WireGuard
 is a great foundation -- but it's lacking critical features like 2FA, SSO, and more that prevent it from being used effectively in team environments.
is a great foundation -- but it's lacking critical features like 2FA, SSO, and more that prevent it from being used effectively in team environments.So we built Firezone.
Firezone's an intuitive, snappy web UI bundled as a Linux package designed to make it as painlesss as possible to manage secure remote access for your team.
Use Firezone to manage secure remote access to applications in your private cloud, funnel traffic through a single egress gateway for your team, establish a reverse tunnel to a host behind NAT, or simply ensure that the first hop from your teams' laptops is encrypted when connecting from untrusted cafe and airport WiFi.
What makes Firezone different?
We're 100% open source and plan to remain that way. We're also self-hosted; we believe virtual private networks should remain private. Firezone can be deployed in air-gapped environments such that none of your traffic ever touches our servers.
What's next?
Firezone is still in its infancy; we've got tons of new features in the pipeline for release later this year. Now's a great time to check it out and offer your feedback to steer development! We just launched our public Beta program and will be giving early adopters license keys to paid Firezone tiers when they become available. Register to receive yours! https://e04kusl9oz5.typeform.com...
@marcusquinn Agreed - I did a bunch of comparison on these two as well before landing on Netmaker. I find Netmaker still in active "try things" development which may make people a bit skittish for production, but aside from the occasional ballooning hosts file size (which has been fixed recently), it's been pretty stable. Some issues with CGNat but that's because CGNat is shit, not their fault.
I also really like that it's about as low level as it gets - it's really just coordinating wireguard tunnel updates from a central console. Fantastic "simplicity" without the fuss.
Haven't gotten "external clients" figured out yet, and the windows app is still rough, but Linux on Linux is solid across clouds.
-
Sorry, I made a duplicate post. Any way we can merge the votes on this?
-
Sorry, I made a duplicate post. Any way we can merge the votes on this?
-
 G girish referenced this topic on
G girish referenced this topic on
-
 M marcusquinn referenced this topic on
M marcusquinn referenced this topic on
Hello! It looks like you're interested in this conversation, but you don't have an account yet.
Getting fed up of having to scroll through the same posts each visit? When you register for an account, you'll always come back to exactly where you were before, and choose to be notified of new replies (either via email, or push notification). You'll also be able to save bookmarks and upvote posts to show your appreciation to other community members.
With your input, this post could be even better 💗
Register Login

