Here's my guide on how to run your local Cloudron from home or office through a public reverse proxy server on a VPS in the 'Cloud' through Tailscale. No port forwarding or network acrobatics are required!
Prerequisites
- VPS
- You don't need much for this: 1 CPU, 1GB RAM and minimal disk space
- Pay attention to the IP allocation and bandwidth allowed!
- Locally hosted Cloudron VM (fresh install)
- A domain name to use with the install
- At least 100mbps uplink to the Internet
Simple overview
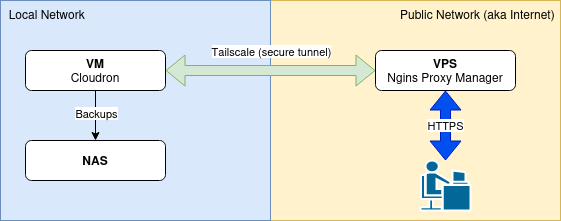
Set up and configure the VPS Proxy Server
Procure and configure the VPS in the 'Cloud'. I use Vultr.com and you can get a $100 credit for two weeks to test things out (affiliate link) or DigitalOcean.com for $200 for 60 days (affiliate link).
I use Debian 12, but you can choose Ubuntu or something similar. Not tried it with RedH*t or Arch.
Ideally, you should get a VPS with direct access to the internet and an IPv4 address. Watch out as some providers try to save costs, and IPv6 and network shenanigans are out of the scope of this tutorial.
Install Docker: (ref. https://docs.docker.com/engine/install/debian/#install-using-the-convenience-script)
curl -fsSL https://get.docker.com -o get-docker.sh | sudo sh get-docker.sh
You may need to install docker-compose separately:
sudo apt install docker-compose
Pull Nginx Reverse Proxy (or your preferred reverse proxy with Let's Encrypt SSL). I use Docker Compose to keep things neat. You can find out more here: https://nginxproxymanager.com/setup/#running-the-app.
Configure your firewall - I use the one at the provider - to only allow ports 80 and 443 to the public. Wall-off SSH (22) and the Nginx Proxy Manager's admin port (81) by only allowing access from your home/office IP(s) and or Tailscale network.
Install Tailscale and set it to accept routes (this is key):
curl -fsSL https://tailscale.com/install.sh | sh
Get Tailscale online and accept routes (important!):
sudo tailscale up --accept-routes
Make sure you have restarted and tested. You can see your node in the Tailscale control panel, and the routes have been enabled.
Ready? Let's go local.
Prepare the server for Cloudron
Install a fresh VM (ideally) with Ubuntu 22.04 (boo!).
Set your VM's IP to be fixed via DHCP or manually, as we don't want it to change again.
Install your favourite tools, such as mc and qemu-guest-agent (if you're using Qemu/Proxmox), git, and curl.
Ensure you install Tailscale on the server and run it with the option to expose its route using the local IP:
sudo tailscale up --advertise-routes=192.168.X.X/32
Log in to the Tailscale control panel and enable the route!
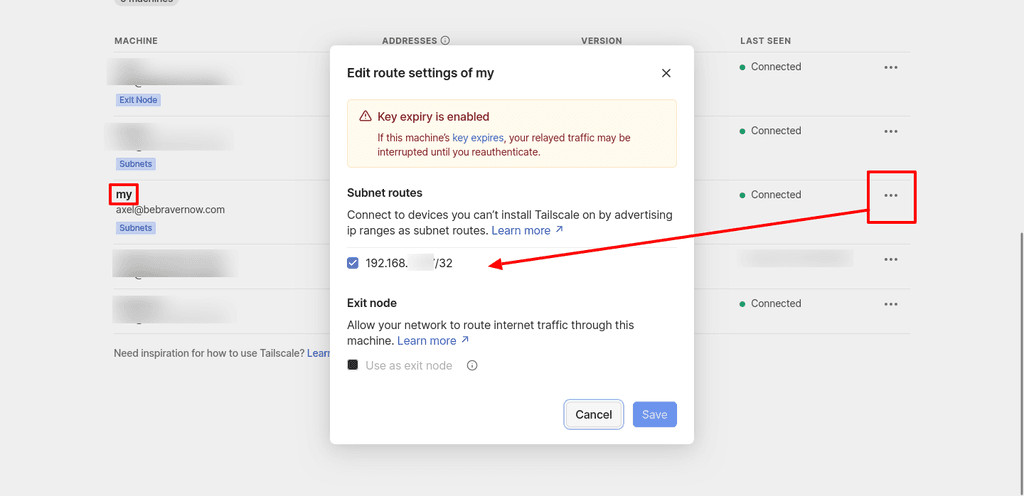
Log on to your VPS and ping the VM's local IP to ensure our proxy can access the server.
ping 192.168.X.X
All good? If not, return a few steps and make sure your routes are exposed and accepted.
On your DNS for the domain you want to use, create two A Records, one for the root domain and one wildcard, both pointing to the VPS IP address.
On the VPS, login to Nginx Proxy Manager (http://<IP of VPS>:81) and create a wildcard SSL certificate for the domain (*.example.com).
Create a new reverse proxy entry using both the root and wild card, pointing at https://<local IP of your VM>:443.
Install and configure Cloudron
Head over to the local VM and install Cloudron (finally).
wget https://cloudron.io/cloudron-setup && chmod +x ./cloudron-setup && sudo ./cloudron-setup
Once installed, reboot and log on to the configuration wizard (https://<local IP>/).
Now come the critical bits, which took me some trial and error. Be sure to snapshot the VM before you continue to avoid reinstalling everything in case you make a mistake!
- Domain: your root domain (e.g. example.com)
- DNS Provider: whatever you are using or set it to manual and tweak it later
- Zone Name: leave it as it is (should show your root domain)
- Certificate Provider: set this to 'Self-signed/Custom' and upload the certs provided by the Nginx Proxy Manager from earlier. They'll download in a ZIP archive. You will need:
- fullchain1.pem and privkey.pem respectively
- ref. https://docs.cloudron.io/certificates/#custom-certificates
- IP Configuration: select 'Static IP Address'
- IP Address: enter the public IPv4 address of your VPS (not the local one of the VM)
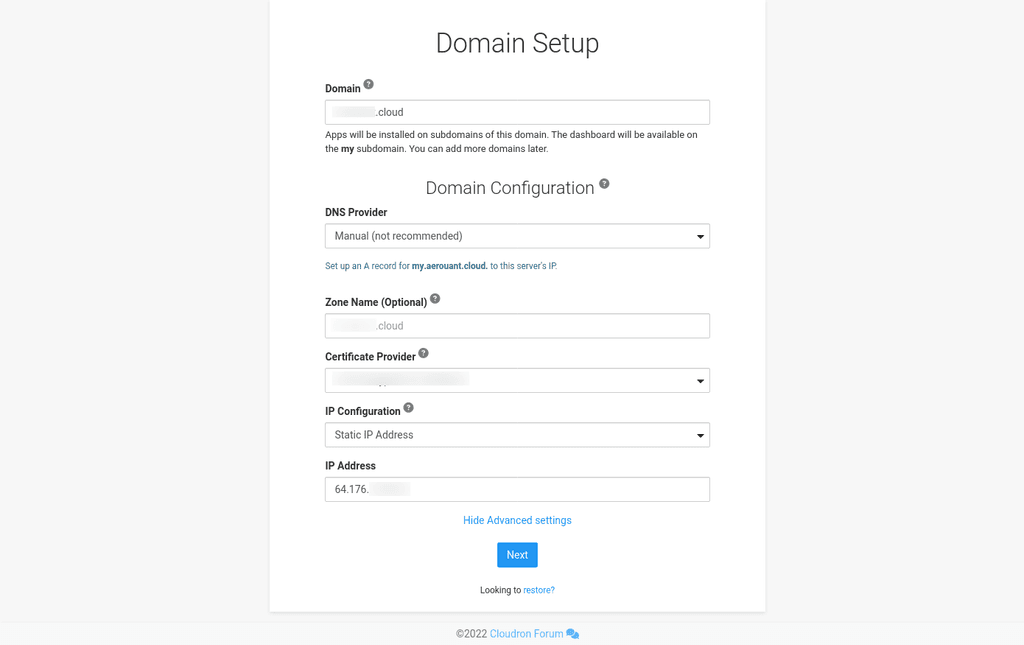
If you are sure you have taken a backup/snapshot of your VM at this point, be braver and hit the 'Next' button.
It will take a while to check itself and present you with the Cloudron account set-up screen. If not, watch for errors in the log file (the path is shown on the screen).
If all goes well, browse my.<your domain>.<tld> and log in. If not, restore to the snapshot and try again. Feel free to post your comments and questions below, and I'll do my best to help.
Finalise the set-up
Once logged on, head to settings and set up the backups. I use a local Samba share from my NAS and rsync (no encryption as the volume is already encrypted). This should make for fast, local backups. I just entered my local NAS IP address (e.g. 192.168.x.x) and login details. Remember that while Cloudron is served from behind the proxy on the VPS, the actual Cloudron server is on your local network and you can point it to local services 
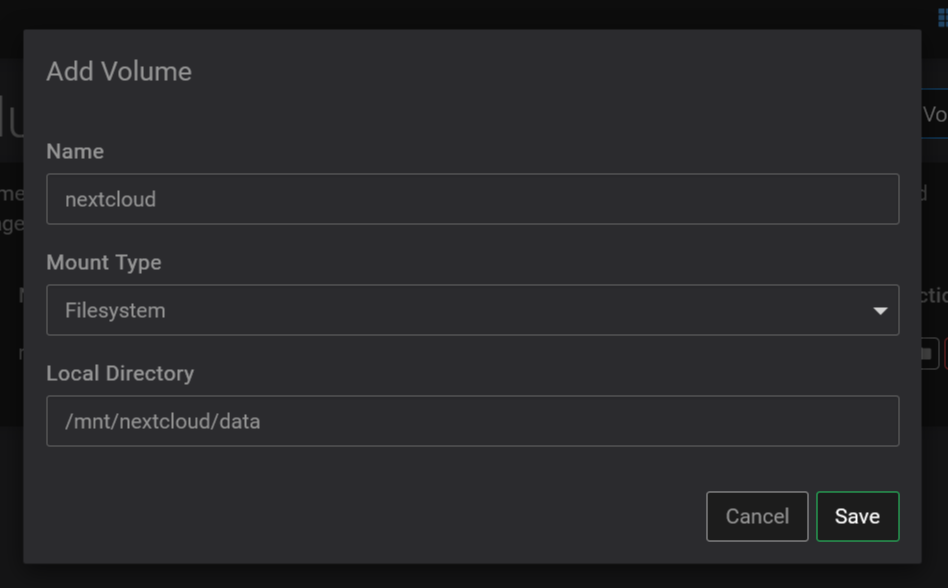
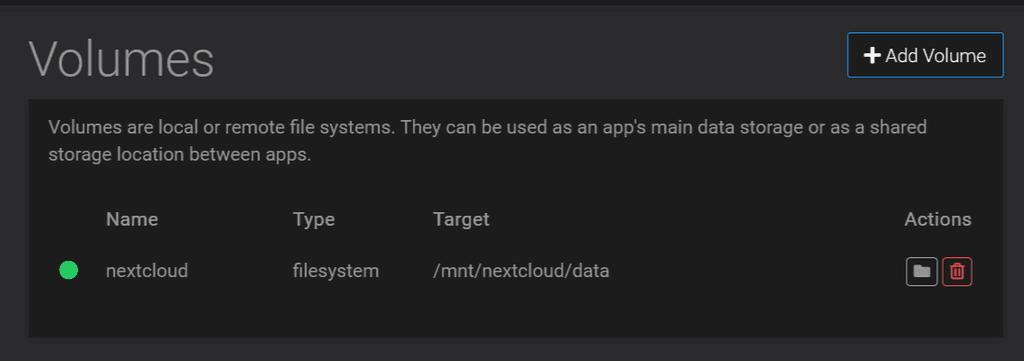
You can also set up other volumes on your NAS for photos or other stuff.
Check the email set up for our primary domain is working and it is probably showing some red marks if you chose manual DNS set up. In this case, head to your DNS and create the missing records shown in the error messages.
The reverse DNS entry (PTR record) will fail unless you change it on your VPS provider's DNS (where available). While you can host multiple Cloudrons behind the same Nginx Proxy Manager and IP, if you care about performance and email deliverability, I recommend a separate VPS and IPv4 for each or ignore the error and use an external bulk SMTP service like SMTP2GO or Mailgun.
Fin
Ensure everything you need is green, and double-check the error logs for messages. Once you are happy, install an app and enjoy your new Cloudron 
Up next
The next part of this guide will focus on using Tailscale to access the Cloudron service locally without going out of the network and back in again. One of the strengths of Tailscale (and similar services) is that it can connect services directly for lower latency and increased performance.
Let me know what else you would like to see. I post this primarily as a note to myself and share it hoping you found it helpful.
Please note
Let me know your questions or comments on how I accomplished this, and note that I am not affiliated with any of the service providers, Cloudron, or companies mentioned unless stated otherwise.
The help I provide on this forum is free and constitutes my opinion, not that of my employer. Professional services are available via the link in my signature - I cannot provide any paid support in this forum. No warranties are provided or implied.
Document version control
- 2024-04-27 - v.1.0 - Initial version



 can we have more options to customise the dashboard, please?
can we have more options to customise the dashboard, please? 







 notion but never liked the fact I rely on a third party service for some personal data.
notion but never liked the fact I rely on a third party service for some personal data.