@girish do we have a way to do this yet? Support for reverse proxies in front of cloudron?
Mastadamus
Posts
-
Please include ability to serve HTTP unencrypted over port 80 for network traffic inspection purposes -
VLAN : on Opnsense or switch or both?@timconsidine if you want to route between the vlans and push them through the firewall you'll need to do a router on a stick configuration. That is where opnsense vlans will come into play. Unless u have a layer 3 switch.
-
FreeTAKServer for ATAK - Mesh Geo Information SystemI would absolutely love and use the hell out of this. heck i'd pay a bit for this.
-
X-Forwarded-For Header@girish Any update on support reverse proxy or adding this logging config as default?
-
Script to check nginx access logs for 403, 404 and check IP's with greynoise API then send to cloudflare.@girish Gotcha but as long as I don't do that, I should be gtg. Im just thinking of a script that does 3 things.
- Grabs all the IP's from emerging threats block list
- Grabs all the 403/404's from access logs sends them to greynoise to check if they are known "noise" and then
- Add both of these IP groups to that file and restart the service.
-
Script to check nginx access logs for 403, 404 and check IP's with greynoise API then send to cloudflare.@girish If I add IP's to /home/yellowtent/platformdata/firewall/blocklist.txt will the automatically be blocked or will I need to restart the box service?
-
Script to check nginx access logs for 403, 404 and check IP's with greynoise API then send to cloudflare.@micmc Yes you could easily take this script and use it for apache. The only think you need to do is look at your apache logs and see what position the source IP is in. the parts in the script where it does
awk '{print $1}'etc. are telling it to grab the first position in the nginx log which happens to be the source IP for my particular logging configuration. so really the only think you would need to tailor/alter is the awk statements. -
Script to check nginx access logs for 403, 404 and check IP's with greynoise API then send to cloudflare.@fbartels greynoise just runs a big honeypot and sensor landscape that captures and catalogues internet scanning. whereas crowdsec is a community sourced reporting of both scanning and malicious actions. Greynoise I believe has a much larger dataset. Its primary purpose is to see if an IP is targeting just you or multiple entities.
-
Script to check nginx access logs for 403, 404 and check IP's with greynoise API then send to cloudflare.@robi let me look into it. Need to see how I would interact with that list.
-
Script to check nginx access logs for 403, 404 and check IP's with greynoise API then send to cloudflare.I wrote a script that can do the following.
- Check NGINX access.log for 404 and 403 response codes
- Extract IP's associated and see if they are scanners/noise with the community greynoise API.
- If they are noise, you can pass a -c flag and send them to a cloudflare IP block list to decrease "noise"
- If they aren't classified as noise, it can then search the access logs for all activity by these IPs. It will then give a unique count of each URL attempted to be accessed and the response code so that you can perform long tail analysis.
You can find it here. Feel free to use/cut/slice tailor to your liking
https://dev.azure.com/Mastadamus/_git/Cloudflare WAF Scripts?path=/GrabIPandCheck.sh
-
Script to automatically update cloudflare ip blocklistI wrote a script to update an ip blocklist in cloudflare. Even free cloudflare can have 1 free ip list. My script pulls down the emerging threats ip list, grep out the ip and then posts each one via the cloudflare iplist api.
You can adapt this script to retrieve ips from your fail2ban jail and then send them to cloudflare for block.
Feel free to adapt as you see fit
https://dev.azure.com/Mastadamus/_git/Cloudflare WAF Scripts?path=/README.md&_a=preview
-
Cloudron external ldaps with OpenCTII haven't had a chance to finish the overall guide for the cloudron specific part but I completed a guide for installing OpenCTI with Traefik, Elasticsearch, and lots of plugins. I also have a complete docker-compose for OpenCTI, Elasticsearch cluster with X-Pack security, and multiple plugins as well as LDAP integration. you can find it here
OpenCTI install guide
https://dev.azure.com/Mastadamus/OpenCTI/_wiki/wikis/OpenCTI.wiki/3/OpenCTI-with-Traefik-Reverse-ProxyOpenCTI GIT that contains my templates
https://dev.azure.com/Mastadamus/_git/OpenCTIIf you just want to skip to how you integrate LDAP with OpenCTI docker-compose I will paste examples below
- PROVIDERS__LDAP__STRATEGY=LdapStrategy - PROVIDERS__LDAP__CONFIG__URL=ldaps://Your.Domain.Name:636 - PROVIDERS__LDAP__CONFIG__BIND_DN={{`cn=admin,ou=system,dc=YourLDAPserverName`}} - PROVIDERS__LDAP__CONFIG__BIND_CREDENTIALS=XXXXXXXXXX - PROVIDERS__LDAP__CONFIG__SEARCH_BASE={{`ou=users,dc=YourLDAPserverName`}} - PROVIDERS__LDAP__CONFIG__SEARCH_FILTER={{`(cn={{username}})`}} - PROVIDERS__LDAP__CONFIG__MAIL_ATTRIBUTE=mail - PROVIDERS__LDAP__CONFIG__ACCOUNT_ATTRIBUTE=givenName - PROVIDERS__LDAP__CONFIG__ALLOW_SELF_SIGNED=true - PROVIDERS__LOCAL__STRATEGY=LocalStrategy -
Wordpress developer site shows non updatedNVM I found a thread that answer this. Based on my current understanding, the cloudron dashboard shows cloudron package updates. For wordpress core in developer edition we have to control that update.
-
Wordpress developer site shows non updatedIn my cloudron dash it shows that i'm running the latest version of wordpress. Inside my wordpress dashboard though, it shows that i'm running 5.8.4. It prompts me to update it. Which is correct?
-
Please include ability to serve HTTP unencrypted over port 80 for network traffic inspection purposes@girish Yeah thats what I do for my actual job, but it does introduce a ton of issues. 1. You can decrypt if you are using Diffie Helman. As far as I can determine currently the cloudron only accepts ECDH algorithms. This would prevent decryption since you can't MITM diffie hellman as far as I know.
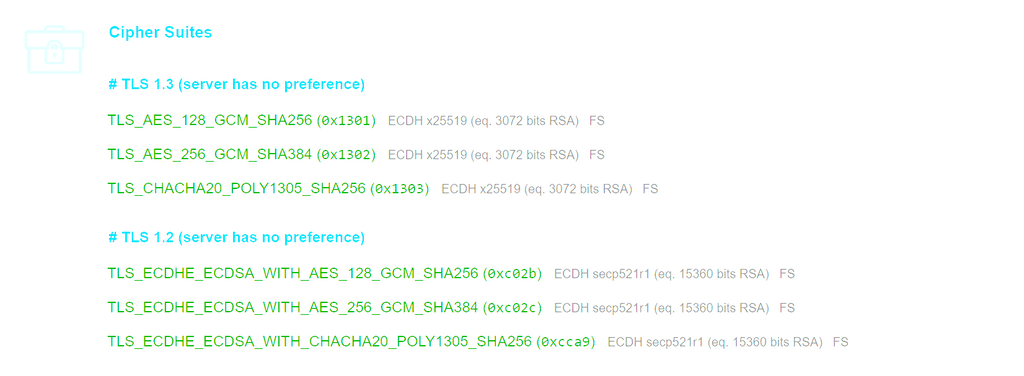
-
Something like ngrok?what about cloudflare tunnels?
-
Training or instruction on creating Wordpress sites?@mehdi Yeah WordPress is targeted frequently for sure. I think there are ways to harden it relatively speaking but it is a risk. I do think its similar though to "not using windows" because windows is so ubiquitous that tons of malware devs write for windows systems. I will check out Ghost though. Thank you.
-
Training or instruction on creating Wordpress sites?Does anyone have any recommendations on solid resources to get proficient at creating Wordpress sites? I know how to stumble my way through it, but I'd like to get better as i'm considering starting a small side business building, securing, and maintaining websites for some local businesses. Has anyone made this a viable business? If so any recommendations? I just want to do it for some local businesses I know of that are in sore need of some web facing information and would benefit from basic cybersecurity.
-
Please include ability to serve HTTP unencrypted over port 80 for network traffic inspection purposesFor those of us who wish to capture our network traffic for inspection, It makes more sense for us to put a LB/reverse proxy in front of our cloudron and then terminate SSL/TLS at the LB and pass un encrypted to our Cloudron. Obviously for certain traffic where E2E encryption is preferred we can proxy pass https. It would be nice if we had the ability to maybe select whether or not we want to also serve on port 80.
-
Cloudron external ldaps with OpenCTI@BrutalBirdie I am working on it now and when I get done I will post it.
